Contents:
- Foreword
- Setting the scene
- Customer challenges and obstacles
- Increased business pressure to use AI across the IT environment
- Data security and privacy
- Complexity and skills shortage
- Identity and access management
- Growing privacy, regulatory and compliance requirements
- Summary of best practices
- Why CyberCX for Secure Cloud & AI
- Case Study: MyHR
- FAQs
- Talk to a Cloud & AI Security Expert
Foreword
In today’s digital era, the race to innovate has led organisations across industries to embrace cloud computing and Artificial Intelligence (AI) as essential drivers of competitive advantage.
Over the past five years, we’ve witnessed a rise in cloud adoption, propelled by the need for scalable, efficient, and secure infrastructure. At the same time, AI has surged as a frontier for business-critical technology, reshaping operations, customer engagement, and decision-making.
Too often, organisations underestimate the complexity and exposure that cloud and AI solutions introduce. As threat actors evolve their tactics and amplify their attacks, cloud platforms remain high-value targets — especially given their vast repositories of sensitive data. With AI now within reach of even unsophisticated adversaries, the landscape of cyber threats is expanding at an alarming pace.
CyberCX is the leading provider of professional cyber security and cloud transformation services across Australia and New Zealand. Our Cloud Security and Solution (CS2) practice partners with multiple cloud providers to offer customised transformation solutions that meet the unique needs of customers. In 2024–25, our integrated approach to cloud and security transformation empowered over 230 organisations — spanning the private, public, and not-for-profit sectors — to successfully design, build, and manage secure cloud and AI environments tailored to their evolving needs.
Through our depth of experience, CyberCX has observed several trends with respect to challenges and obstacles faced by organisations innovating with cloud and AI, including:
- The growing pressure to embrace AI;
- The complexities of managing data security and privacy;
- A shortage of IT skills;
- The difficulties in managing identity and access permissions across platforms; and
- Evolving privacy and regulatory requirements.
This report explores these five key challenges facing organisations adopting cloud and AI technologies and delivers practical guidance to help navigate complexity, mitigate risk, and unlock the full potential of secure transformation.
David Johnston
Executive Director, Cloud Security and Solutions, CyberCX
Setting the scene
As the global cyber threat landscape continues to deteriorate, adversaries are evolving their tactics and upping the tempo of attacks. CyberCX has observed the following key trends impacting cloud & AI security:
Cloud environments are a high-value target for cybercriminals as they hold a wealth of sensitive information and have a broad attack surface particularly when integrated with third party services. Additionally, the shared responsibility model that applies to cloud services may lead to ambiguity or complacency in relation to security control implementation if not clearly defined, increasing vulnerabilities that can be exploited.
AI-powered threats continue to rise with the acceleration of AI capabilities and adoption, including within cloud environments. The accessibility of AI means that amateur cybercriminals can now devise sophisticated and novel cyber attacks. CyberCX’s 2025 Threat Report linked threat actor use of AI technologies to the rise in Business Email Compromise (BEC) incidents. Simultaneously, however, AI is increasingly being harnessed to detect and respond to cyber attacks in a more effective and timely manner.
Sophisticated ransomware attacks continue to affect organisations and individuals. Cybercriminals are increasingly exfiltrating sensitive data, and demanding payments in exchange for restoring access.
Increased use of Shadow IT and Shadow AI as a result of improved accessibility and convenience of cloud Software-as-a-Service (SaaS) offerings. Here, employees opt for tools and services with enhanced usability or features without the required authorisation. The lack of visibility over these services means that organisations are unable to implement appropriate security controls.
Growing insider threats pose a significant challenge to private and public sector organisations, given insiders’ intimate knowledge of systems and data. Insider threats can arise from both inadvertent or deliberate and malicious actions. As organisations continue to adopt cloud and hybrid technologies, their environments may become increasingly complex and difficult to manage. Existing cyber security processes and controls may no longer be sufficient to manage these environments.
State-sponsored cyber attacks are expected to increase against the backdrop of international instability and complex strategic operating environments for Australia and New Zealand. Attacks of this nature may target critical infrastructure including telecommunications organisations and energy systems.
While attacks may be carried out directly, they may also be carried out indirectly by exploiting insecure supply chains. As state actors continue to engage in espionage and cyber security reconnaissance to gain a strategic advantage, the techniques for conducting these activities are becoming increasingly modified to cloud technologies.
CyberCX’s 2025 Threat Report highlighted that espionage incidents continued to have a much longer time to detect compared to the previous reporting period.
These shifts in the cyber threat landscape underscore the need to identify and implement appropriate controls and continuously innovate for cloud environments.
Customer challenges and obstacles in cloud innovation
Over the last five years, digital transformation initiatives and growing demand for efficient, scalable, secure, cost-effective infrastructure has driven the rapid adoption of cloud technologies.
Furthermore, the increase of hybrid and remote work across private and public sectors has led to an increased reliance on cloud technologies to facilitate business operations. While accelerated adoption of cloud technologies has supported productivity and flexibility, it can also introduce risks.
Through CyberCX’s extensive work assisting companies with cloud strategy, design, migration, and security, we have observed several trends with respect to challenges and obstacles faced by organisations.
Customer challenge and obstacle 1:
Increased business pressure to use AI across the IT environment
With the business world under growing pressure to embrace AI, many organisations now view it not only as an option, but a necessity for the continued success of operations. Our customers are experiencing increasing demands from stakeholders to use AI-driven insights to boost efficiency, reduce costs, and uncover new market opportunities. Additionally, as the prevalence of AI gains prominence in mainstream society, consumers are increasingly expecting personalised experiences.
Larger businesses are seeing the value of AI and are investing accordingly.
– New Zealand’s AI Strategy, Ministry of Business, Innovation and Employment.
While organisations may be eager to harness the benefits of AI, its use also brings challenges in relation to data security and privacy that must be considered.
- AI technologies rely on vast amounts of information, which is typically stored in a centralised manner on the cloud. Access to such information is amenable to crafting cyber security attacks.
- Reliance on AI-generated decisions may lead to biased and/or erroneous outcomes, particularly where datasets are skewed. The ability to understand and challenge decisions may also be hindered where algorithms are considered proprietary and not disclosed.
- Additionally, organisations must also consider the possibility of cyber incidents arising from inadvertent disclosure of confidential or personal information, if users do not fully comprehend how the information they upload to AI systems will be used and shared.
While many businesses have some form of AI governance, there is still a need for clearer guidelines and standards.
– AI in action: Exploring the impact of Artificial Intelligence on New Zealand’s Productivity, AI Forum New Zealand, March 2025.

Customer challenge and obstacle 2:
Data security and privacy
With the acceleration of cloud and AI computing, many customers are finding data security and privacy increasingly challenging to manage for the following reasons.
Increased risk of data breaches
Advanced data analysis relies on vast amounts of data, increasing the potential for information leaks if not appropriately secured. Centralised storage of data in the cloud further exacerbates the risk of being targeted by adversaries.
Using AI services in the cloud introduces further risks to data security. If AI datasets are not appropriately sanitised, AI models may memorise and leak sensitive information.
Additionally, cyber actors may be able to exfiltrate data through reverse-engineering AI models.
Unauthorised disclosure of data may also occur inadvertently if organisational personnel upload sensitive information to public models. This is often a result of personnel not completely comprehending the data privacy and security risks of using AI.
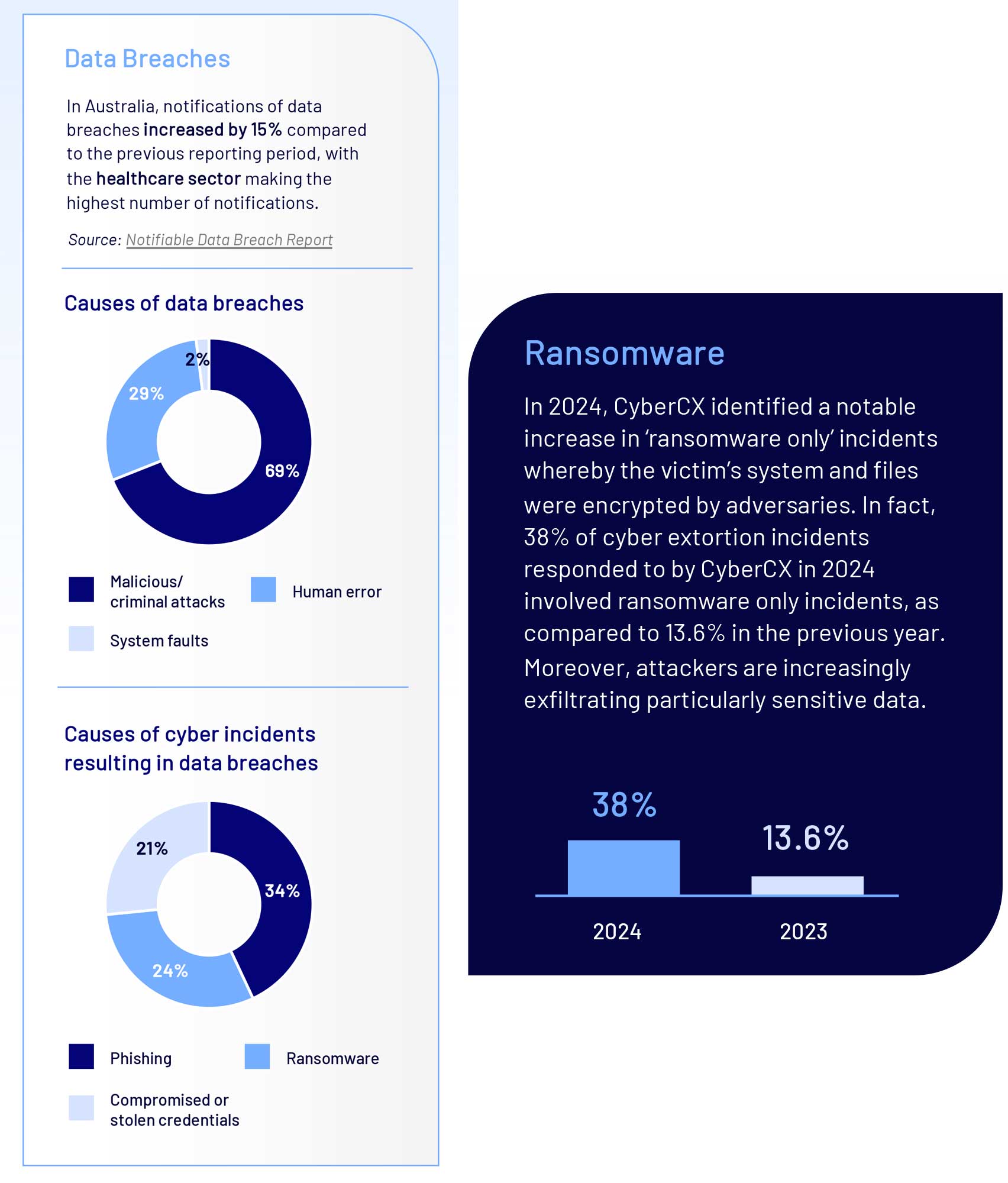
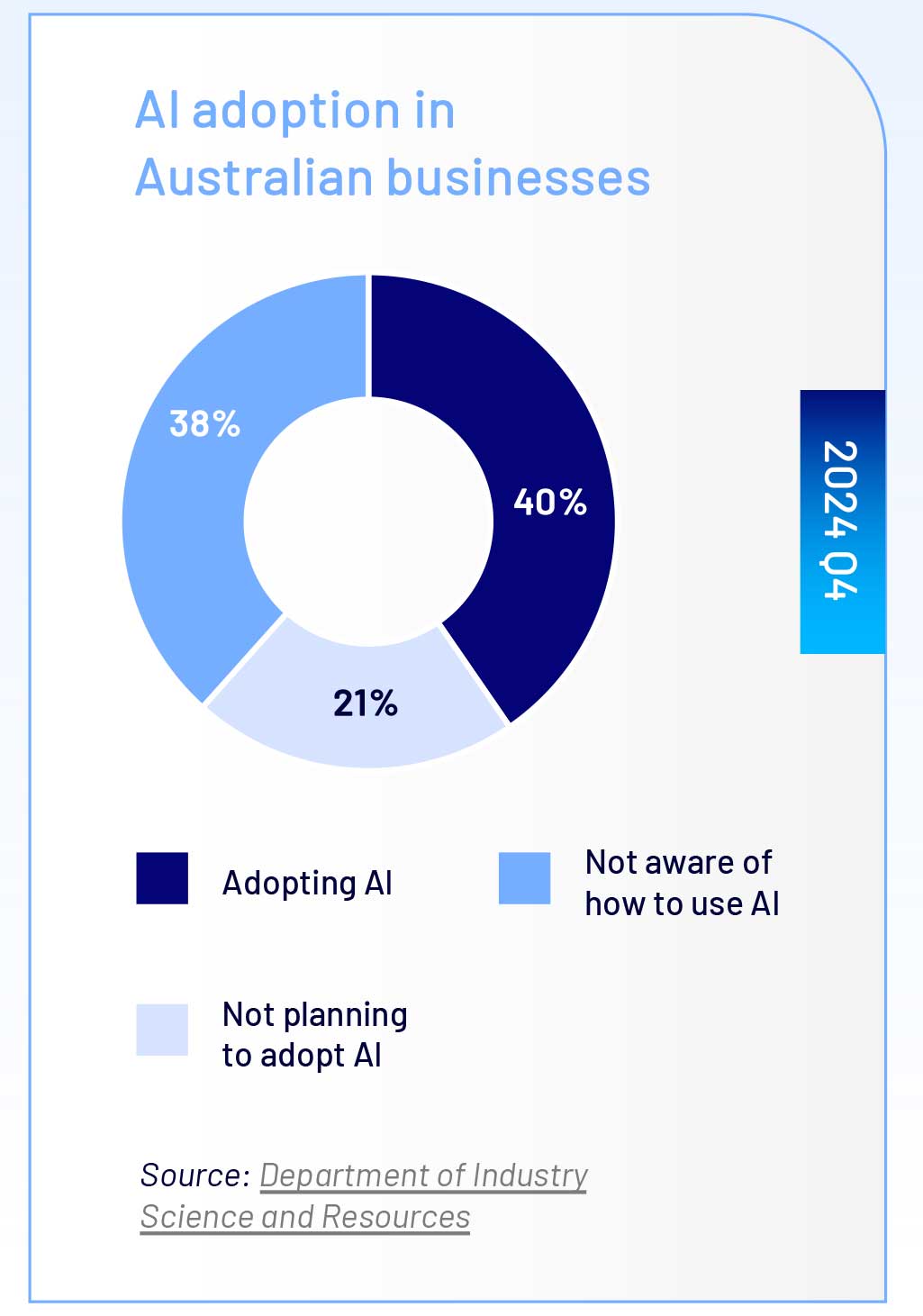
These statistics underscore the need for organisations to devise and implement appropriate governance and technical controls to prevent and appropriately respond to incidents when they arise, including by fostering cyber security and privacy awareness amongst staff.
Loss of direct control over data
The use of third-party cloud services often results in loss of direct control over data. Cloud consumers are reliant on the security posture of cloud service providers and their products/services, across various domains including backup and recovery, physical security, virtualisation security, and data encryption. We encourage customers to undertake security assessments of those cloud services to ensure the requisite level of assurance throughout the vendor lifecycle.
Data residency and sovereignty
Cloud service providers, including hyperscalers, are domiciled in various parts of the world which may create risks in relation to data residency and data sovereignty. Data residency options which restrict the storage and processing of data within the cloud consumer’s specified region, may not be available. For example, data may need to be sent offshore to support services that operate globally and in failover scenarios. Further, telemetry data may also be sent offshore for global processing.
If cloud service providers store data offshore, the customer data they hold may be subject to the laws and regulations of foreign jurisdictions. This may result in foreign governments accessing data, resulting in loss of control over data and concerns surrounding confidentiality.
Data retention and disposal
The Archives Act 1983 and the Public Records Act 2005 contain data retention requirements that apply to Australian and New Zealand entities respectively. Determining retention and disposal requirements involves an assessment of business needs, accountability requirements and community expectations. Guidance from the National Archives of Australia notes that entities should be aware of risks associated with outsourcing data storage. This includes challenges associated with ensuring that disposal actions are transparent and appropriately carried out. Cloud storage has inherent data retention challenges, as it creates multiple geographically distributed copies of data to support availability.
Data portability
Organisations should consider that access to information may be lost if the cloud service provider ceases the provision of services. The cloud consumer may also wish to unsubscribe from the service. To ensure the cloud consumer’s data is not lost in these scenarios, we advise organisations to have contractual security controls in place to ensure they can export their data.
Supply chain risk management
Cloud service providers may leverage subcontractors to deliver their services, over which cloud consumers may have limited visibility, if any. This creates the risk of unauthorised access and disclosure of customer data, particularly if the subcontractor’s security controls are not commensurate with those of the cloud service provider.
API security
Cloud services typically rely on Application Programming Interfaces (API) to facilitate communication. Poor API controls have contributed to notable data breaches in recent years, highlighting the importance of securing APIs including through authentication and encryption.
Insider threats
The above challenges are exacerbated by risks associated with insider threats. Organisational personnel have elevated access to data and systems, including customer data and confidential commercial information. Aggrieved employees may be tempted to use this data in retaliation against their employer, colleagues or customers.
Inference of personal information by AI
AI may be used to build customer profiles, including by inferring personal information through the aggregation of data, especially if organisational data boundaries are not adhered to. Issues of consent may arise if individuals are not made aware of or do not fully understand how their personal information may be used and disclosed by AI.
Customer challenge and obstacle 3:
Complexity and skills shortage
Organisations worldwide continue to be affected by IT skills shortages. This gap is particularly prominent in multi-cloud and AI domains, where technological advancements and rapid adoption are outpacing skills uplift. Rapid adoption has been fuelled, in part, by the shift to remote working arrangements which relies on cloud computing. There is also the added business pressure to use AI and cloud for strategic advantage.
We have observed that an absence of suitably skilled resources can result in a myriad of issues. These include security vulnerabilities due to system misconfigurations, compliance issues, underutilisation of cloud and AI features, deployment delays, performance and quality degradation, reduced customer satisfaction and ultimately loss of revenue.
Multi-cloud environments
Multi-cloud environments enable customers to take advantage of the features offered by various cloud service providers. However, multicloud environments also bring a host of challenges relating to integration and security.
To manage these complex environments, organisations must find and retain staff who are skilled across administering various platforms, designing cloud and security architecture, infrastructure-as-code for various platforms, and orchestrated containerisation. Such skills can take years to develop and require ongoing uplift to keep pace with technological advancements and changes to service offerings.
AI skillsets
Skills shortages are expected to exacerbate as cloud services are increasingly leveraged for AI and big data computations. To support the secure and ethical implementation of AI, organisations must be able to attract, retain and train resources who are sufficiently skilled in deploying Generative AI, predictive analytics, Large Language Models (LLMs), machine learning, and Natural Language Processing (NLP), against a backdrop of evolving regulations, operational and security requirements.
While we are seeing organisations attempt to fill skill shortages by training employees in this area, it can often be hampered by time and budget constraints in the short-term.
Skills shortages are expected to exacerbate as cloud services are increasingly leveraged for AI and big data computations.
Customer challenge and obstacle 4:
Identity and access management
Complex cloud environments increase the difficulty involved in managing identities and access permissions across platforms. Poorly managed identities can lead to unauthorised access and data theft or modification.
Integration with on-premise Identity and Access Management (IAM) systems
Integrating on-premise domains with cloud identity providers requires mapping of roles and permissions, which may be tedious and prone to
misconfigurations that result in unauthorised access.
Integration can be particularly challenging with AI systems, which may be incompatible with traditional IAM systems. This may require significant investment in terms of reengineering.
Dynamic and scalable resources
We often find that existing IAM models for on premises environments are not always suited for the cloud. Cloud computing involves ephemeral resources that are spun up or down in response to fluctuations in resource demand. IAM systems must be able to provision and deprovision permissions for such resources in real-time.
Manual vs automated access management
Managing identities across their lifecycle can become challenging without the use of automated provisioning and deprovisioning. This is particularly pertinent to ephemeral resources which are often provisioned and deprovisioned automatically, making manual access management impractical. These difficulties will exacerbate as user groups proliferate, and access requirements become more complex.
Shadow access
Shadow access can result from the inadvertent granting of permissions through automated workflows and misconfigured cloud services. Automation tools that are not appropriately monitored may create resources and permissions that are not detected. Additionally, IAM roles and policies may be inadvertently inherited across various projects. The use of default settings that favour functionality over security, or are based on the misconception of being inherently secure, may also result in the overprovisioning of access.
Contingency plans
Organisations must have backup authentication mechanisms in place to
avoid losing access to systems in the event their cloud-based identity provider becomes unavailable. We recommend devising backup authentication methods, such as break-glass accounts and local accounts that do not rely on the cloudbased identity provider. Further, procedures should be in place to ensure the swift revocation of access and rotation of credentials.
Insider threats
Organisational personnel are provisioned with elevated access to systems and data to fulfil their job responsibilities. However, access may be misused – whether inadvertently or maliciously – and result in the theft, loss or modification of confidential information. We suggest organisations deploy IAM systems integrated with monitoring and alerting systems that can detect suspicious behaviour from legitimate accounts.
User lifecycle management
Users may retain access to systems for longer than necessary in the absence of regular access reviews and revocation procedures. Access should be reviewed regularly, preferably through an automated mechanism, to identify and disable inactive accounts. Access revocation procedures should also be in place to address changes in employee roles and the end of the employment relationship, including emergency offboarding scenarios.
Using AI to manage IAM
AI IAM systems rely on behavioural analytics, which can produce erroneous outcomes including false positives and negatives. For example, they may incorrectly identify legitimate access as suspicious or fail to identify real threats. This may lead to operational disruptions, unauthorised access and security incidents.
Managing identities in a multi-cloud environment
The accelerated adoption of multi-cloud environments is driven by several advantages including the ability to leverage the best services for specific use cases and meet sovereignty requirements. As each cloud service provider has its own IAM model, it may be challenging to implement consistent policies and increase the risk of misconfigurations. In our experience, visibility across the various platforms as well as integrations with any on-premise systems is essential.
Privileged access exposure
Privileged accounts remain the most valuable target in any enterprise. If compromised, they provide attackers with unrestricted access to sensitive systems and data, effectively bypassing all other security layers. In rapidly expanding cloud and SaaS environments, reducing privilege exposure and establishing clear visibility across high-risk entitlements is essential to any modern cloud security strategy. However, in our experience many organisations struggle beyond foundations to do so effectively and consistently.
Non-human identities
Service accounts, API tokens, machine identities, and automation credentials, now outnumber human users in most environments. These accounts often hold excessive privileges, are hardcoded into scripts, and remain largely unmanaged or poorly secured. As secrets proliferate across code repositories and DevOps pipelines, manual management are no longer sustainable making secrets management and automation a critical cloud security requirement.
Fragmented identity
Rapid adoption of cloud and SaaS platforms has introduced significant identity complexity. User identities are dispersed across disconnected directories, legacy systems, and cloud native applications.
Without unified visibility and governance, organisations are often left with inconsistent security controls, limited assurance of access legitimacy and critical visibility gaps. These siloes weaken Zero Trust foundations and increase exposure to identity-based attacks.
Customer challenge and obstacle 5:
Growing privacy, regulatory and compliance requirements
Privacy, regulatory and compliance requirements are evolving to adapt to the rapid adoption of the cloud. Organisations must consider complex data sovereignty, protection of sensitive data, and data governance issues to ensure that all relevant requirements are met.
Offshore storage of data
Cloud computing enables offshore processing and storage of data. However, certain types of data, such as classified data, may need to stay within specific jurisdictions. Adaptations to system architecture or infrastructure may be necessary to meet these requirements.
Complex regulatory landscape
Organisations must adhere to various data security and privacy regulations, depending on their industry and types of data they hold. For example, in addition to the Australian Privacy Act 1988, operators of critical infrastructure assets must be cognisant of their obligations under the Security of Critical Infrastructure Act 2018 (SOCI Act).
This includes requirements to develop a Critical Infrastructure Risk Management Program (CIRMP) to address cyber security threats, protect data stored in the cloud through appropriate controls such as encryption and access restrictions, and report incidents within 12 hours if considered significant, otherwise within 72 hours.
Australian healthcare providers participating in the My Health Records Act 2012 system must satisfy certain cyber security obligations to protect sensitive information. These include establishing a security and access policy which addresses training and management of user credentials, and reporting data breaches, separate from the Notifiable Data Breaches Scheme under the Privacy Act.
Various state-based legislation further add to the complexity. With the exception of South Australia (SA) and Western Australia (WA), every Australian State has its own privacy legislation.
While state-based legislations are derived from the Australian Privacy Act, they can differ slightly. Additionally, the Australian Commonwealth and every state except WA, has data retention laws that cover thousands of data types. Conflicts in retention requirements between states exist and can often lead to organisations keeping data indefinitely because it is the path of least resistance.
Australian states also have mandatory destruction requirements for certain types of data. This, combined with the proposed Privacy Act’s provision of an individual’s Right to Erasure, further complicate regulatory compliance and data governance.
Implementing supplementary controls or configurations may be required for some organisations to meet the increasingly complex regulatory landscape and compliance obligations.
Evolving privacy regulations
Recent amendments to the Privacy Act have introduced stricter requirements, leading to greater alignment with the European Union’s General Data Protection Regulation (GDPR). This includes requirements for clear, informed and unambiguous consent for data collection and use, explaining how automated decisions using personal information are made, robust security practices, and stronger enforcement powers for the Office of the Australian Information Commissioner (OAIC) as the regulator.
These amendments add to the existing obligations to comply with the Notifiable Data Breaches Scheme under the Privacy Act, requiring notification to the OAIC when a data breach is likely to result in serious harm. While organisations are given a 30-day timeframe to make such assessments and notifications, this can often be cut short when media organisations report on data breaches in the meantime.
Compliance complexity in multi-cloud and hybrid environments
Data governance is particularly difficult to manage in complex multi-cloud and hybrid cloud environments. Each cloud service provider may adhere to different compliance standards, creating inconsistencies in the level of security assurance provided. Further, the use of various environments can make it more difficult to track where data is stored and how it is being used.
Ambiguities of shared responsibilities
Responsibilities for managing the security of the cloud are shared between the cloud service provider and the cloud consumer. Cloud service providers are typically responsible for the security of cloud infrastructure, whereas cloud consumers are responsible for the security of their data within the cloud. However, poorly defined shared responsibility models may give rise to ambiguity leading to security gaps or misconfigurations.
Access to information by foreign governments
The Australia-US CLOUD Act Agreement is a bilateral data sharing framework. It enables US law enforcement to compel US-based technology companies to provide data, regardless of where the data is stored in the world. This means that Australian data hosted by US cloud service providers can be subject to an access request by the US government.
Voluntary AI framework
Australia and New Zealand do not yet have enforceable regulations pertaining to the use of AI. Rather, responsible AI guidance and principles have been published by both countries to encourage safe AI use and innovation. The Responsible AI Index 2024 details how Australian businesses are tracking by evaluating their adoption and maturity of responsible AI practices.
The findings demonstrate that while most organisations believe their AI systems align with Australia’s AI Ethics Principles, less than a third of organisations surveyed have implemented the necessary practices. This demonstrates a clear gap between perception and practice of responsible AI use. Similarly, the March 2025 AI in Action Report produced by the AI Forum of New Zealand highlighted that “while many businesses have some form of AI governance, there is still a need for clearer guidelines and standards.”
Related: Secure AI: Navigating AI Adoption Without Losing Sight of Security
Environmental considerations
There are several environmental impacts that organisations should consider with rapid cloud adoption. Notably, running data centres requires significant energy and water usage.
Although data centres are increasingly adopting energy efficient technologies, the energy demands of AI remain considerable.
Organisations must find ways to minimise the consumption of resources required to develop, train and use AI. Suggestions by the World Economic Forum on reducing the environment impact of AI include leveraging pretrained AI models and APIs, using batch processing, complying with ISO 42001 requirements on climate change, conducting assessments to determine the impacts of particular AI systems and use cases on society, partnering with sustainable vendors, and educating employees to optimise their use of AI given its environmental implications.
Summary of best practices
Addressing these key challenges and obstacles can ensure continued success for organisations in growing and maintaining their cloud footprint.
By implementing robust security measures, continuous monitoring, and compliance with regulations, organisations can leverage the benefits of the cloud while minimising risks.
1. Strategy and domain architecture
Cloud strategy
Clearly defined cloud strategies are necessary to achieve secure cloud adoption that aligns with business objectives. The cloud strategy should define key elements including technical architecture, data integrity, security and culture.
Importantly, cloud strategies should be reviewed periodically to adapt to changes in the business environment and technology.
The CyberCX Cloud Strategic Benchmarking Report highlighted the gap between best practice and implementation, with 45 per cent of customers surveyed having no formal documented cloud strategy.
Data governance
Organisations must establish effective data governance frameworks and policies, to ensure data security and compliance with regulations.
This includes defining roles and responsibilities within the organisation, and policies for data access, sharing, retention, disposal, and quality, based on applicable regulations and industry best practice.
Organisations should periodically undertake data discovery exercises to obtain a comprehensive view of the data they store, its location, and sensitivity. The findings should be reflected within a data inventory, with asset classifications. In our experience, undertaking these activities can help inform appropriate data protection initiatives and adherence to compliance requirements.
Data governance will become increasingly important when deploying AI within an organisation. The accuracy and fairness of content produced by AI relies on the quality of the data that is input.
Defense in depth
Cloud security architecture should incorporate multiple layers of security, also referred to as ‘defense in depth’. This principle is based on the idea that no single control is impenetrable. Therefore, we recommend organisations address several security domains including network security, IAM, encryption, secure software development, monitoring and logging, resting upon strong security governance and compliance foundations.
Zero Trust architecture
Zero Trust architecture is premised on the model of ‘never trust, always verify’. It involves authenticating and authorising each access request, regardless of whether it originated inside or outside of the network. Zero Trust architecture is implemented through a combination of mechanisms including rolebased access controls (RBAC) configured in line with the principle of least privilege, segmenting networks and resources, automation of security policies and remediation, and continuous monitoring and logging.
Authentication can be strengthened through the enforcement of multi-factor authentication using ‘something you know’, ‘something you have’, and ‘something you are’, and ensuring these factors are phishing-resistant.
Infrastructure-as-Code
Infrastructure-as-Code (IaC) can support secure infrastructure deployment and management by minimising manual tasks which can be error prone. By defining infrastructure within code, organisations can ensure consistent deployments across environments. IaC also enables automated scanning to identify vulnerabilities prior to deployment.
Network segmentation
Workloads should be isolated using virtual private clouds, network security groups and subnets, as well as firewalls. By segmenting environments for development, test, staging and production activities, organisations can reduce the likelihood of lateral movement.
Encryption
To protect data in use, at rest and in transit, encryption should be applied using ASDapproved cryptographic algorithms and protocols. The management of encryption keys can be supported using key management services, with regular rotation of keys. Organisations may also consider confidential computing to encrypt data in use.
Robust IAM policies
We advise organisations to implement robust IAM policies to reduce the likelihood of unauthorised access to information and systems. The foundation of good IAM practice is adherence to the principles of least privilege and need-to-know which ensure that permissions are granted based on the user’s job tasks. Management of access through policies also supports scalability and consistent security by removing reliance on manual processes. This is particularly important for automated workflows and service accounts.
Data Loss Prevention (DLP)
Organisations should consider implementing DLP policies and techniques to minimise the risk of unauthorised access, disclosure, modification and disclosure of data. Data identification and classification are foundational elements of DLP frameworks, as it enables the tagging of data based on sensitivity which can then be used to enforce restrictions on access, modification, deletion, and transfer.
Supply chain risk management
Collaboration between procurement and security teams ensures that third-party security risks are accounted for and appropriately managed throughout the vendor lifecycle. This ensures that vendors are thoroughly assessed prior to the procurement decision, security requirements are reflected within the contract, and shared security responsibilities are clearly delineated and
understood by all parties.
Depending on the nature of the cloud service required, organisations may be required to select from a limited pool of vendors. In these scenarios, additional security protections may need to be negotiated with the vendor to arrive at the appropriate risk appetite. Once onboarded, we suggest security teams maintain ongoing visibility of the security posture of vendors through regular security assessments and ongoing contract management.
Cloud Access Security Broker (CASB)
CASB systems enhance the security of cloud services by centralising cloud security management across several platforms. They act as an intermediary security mechanism between users and cloud services. CASBs enforce RBACs by integrating with IAM systems, enforce DLP policies, monitor user activities including the use of shadow IT, identify unusual behaviour including by leveraging AI, and can block malware. They can be integrated through API integration, deployment of agents on endpoints, or through proxies.
2. Optimisation, tuning and guardrails
To ensure cloud environments are scalable, secure and continually follow best practices whilst adhering to an organisation’s budget, it is important to ensure effective optimisation, tuning and guardrails are in place.
Implementation of robust guardrails within a cloud environment ensure that security and compliance are consistently enforced, whilst at the same time preventing misconfigurations and operational risks.
Continual optimisation of cloud environments and associated resources ensures that costs do not significantly rise over time as workload demand increases. This also enables performance improvement by ensuring resources are used effectively. Furthermore, organisations should make a concentrated effort to ensure continual tuning of cloud systems and workloads to meet specific application and organisational needs.
Cloud Security Posture Management (CSPM)
CSPM tools enable continuous monitoring of cloud infrastructure to ensure adherence to best practices, compliance requirements, and organisational policies. Their features include continuous provision of real-time insights into cloud resources and data flows, detection of shadow IT, and identifying insecure configurations.
They can also map configurations to security best practices such as National Institute of Standards and Technology (NIST) and Center for Internet Security (CIS) benchmarks, detect suspicious activity including using AI, and automate remediation. Importantly, CPSM solutions can be used across multi-cloud and hybrid environments, supporting centralised monitoring and management.
Automate compliance checks
Once compliance requirements have been identified, and controls and policies have been mapped, organisations can use tools to automatically scan for deviations.
Compliance automation platforms can be used to automate evidence gathering and generate reports on a regular basis.
3. Threat detection and incident response
Harness cloud-native monitoring tools
Traditional security tools are typically not wellsuited to the cloud. Instead, advanced tooling that leverages AI and automation is required to continuously monitor, identify, and respond to anomalous activity in real-time. Cloud-native services that are tailored to each cloud platform are also available and can provide a more seamless alternative.
Centralised security monitoring and control
Obtaining a holistic view of threats across multicloud and hybrid environments can be particularly challenging. Centralising security monitoring can provide unified visibility by aggregating events across all infrastructure and thereby enhance the ability to detect and analyse incidents. By reducing the number of platforms that need to be monitored, security teams can also operate more efficiently.
AI-based monitoring
Integrating AI with security information and event management (SIEM) platforms can enhance the correlation and analysis of logs and user behaviour. The ability to analyse significant volumes of data almost instantaneously enhances the timely detection of threats. This particularly benefits large organisations which require monitoring of numerous endpoints and cloud services.
Given AI’s ability to learn from new data, the use of AI can allow monitoring systems to evolve to new attack techniques. AI can also be integrated into security orchestration, automation and response (SOAR) platforms to initiate automated responses and prevent the propagation of adversaries in a timely manner.
Ensure cloud service providers give access to logs
As cloud providers manage the underlying infrastructure, cloud consumers do not typically have visibility of related logs, telemetry and network traffic. They are therefore reliant on the cloud service provider to implement effective threat detection and response capabilities. Cloud consumers should ensure the right to access logs pertaining to their cloud tenancies and data is stipulated within contract.
Extended Security Orchestration, Automation, and Response (XSOAR)
XSOAR systems provide several benefits in cloud environments, particularly where multiple cloud platforms are in use. They enable centralised orchestration across cloud platforms, providing visibility across workloads and streamlining response activities. XSOAR also allows for the automation of cloud security operations, helping prevent and contain incidents in a timely manner.
Insider threat mitigation
Insider threats refer to the risk of personnel using access to data or systems in a way that causes harm to the organisation, either maliciously or inadvertently. Personnel may develop malicious intent in the pursuit of revenge, coercion, ideology and even ego. Insider threats can be particularly difficult to detect as personnel are granted legitimate access to systems and have intimate knowledge of organisational processes.
Robust security controls can reduce the likelihood of personnel accidentally or deliberately accessing, disclosing, sharing, or destroying data in a manner that is not authorised. This includes restricting removable media, outbound emails and file shares, maintaining backups of data, enforcing strong password requirements and multi-factor authentication.
Implementing access controls can also reduce the likelihood of an insider threat. This may include access controls based on the principle of least privilege and need to know, as well as adopting a Just-in-Time access model and reviewing access regularly.
Organisations should conduct logging and monitoring of user activity and securely store these logs so they are not tampered.
Robust security controls can reduce the likelihood of personnel accidentally or deliberately accessing, disclosing, sharing, or destroying data in a manner that is not authorised.
4. Data protection
Alignment with best practice guidance
Organisations should keep abreast of developments in relation to government regulations on AI and industry best practice, and consider implementing these, including when they are of a non-binding nature.
Domain specific AI models
AI hallucination refers to the erroneous outputs produced by AI tools which can be caused by inaccurate or incomplete training data. Domain specific models can lower hallucination risks associated with general models, as they are trained using data specific to a certain field or industry, such as healthcare or finance.
Security assessments of cloud service providers
Cloud consumers are reliant on the security posture of cloud service providers and their products/services, across various domains including backup and recovery, physical and virtualisation security, and data encryption. Security assessments of those cloud services are necessary to provide the requisite level of assurance.
Data retention and portability
Organisations must ensure that contractual security controls are in place to export the customer’s data from the cloud service provider’s cloud services and ensure the cloud service provider deletes the customer’s data once subscription has ended.
In line with the Archives Act, Australian entities should understand their data retention requirements and risks associated with outsourcing data storage through the cloud.
Incident and data breach response processes
We advise organisations to establish cyber security incident and data breach response plans and processes. These support the timely detection and analysis of events, a structured and coordinated approach to response activities, containment of incidents, notification to relevant parties including regulators and affected customers in line with applicable regulations, as well as continuous improvement to prevent recurrence.
Organisations should also ensure that suppliers are obligated to swiftly notify them of any incidents affecting their data or cloud tenancies, for example by stipulating this within contractual arrangements.
Backup and disaster recovery
Organisations should ensure that critical data is identified and backed up to prevent loss and support business continuity in the event of a disaster. The disaster recovery procedures should be tested regularly to ensure their efficacy and awareness among staff.
Continuous monitoring and auditing
Continuous monitoring and auditing of activities within cloud environments is imperative for detecting unusual activity in a timely manner. SIEM and SOAR tools can be used to automate detection and response activities. Alerts should also be configured to notify relevant personnel of any detections.
Train AI models based on verified data
AI models should be trained on datasets that have been verified to avoid the generation of biased or erroneous outcomes, also referred to as ‘AI hallucination’. This can spread false narratives, result in poor decision-making, and even compliance risks. It is important that datasets are accurate and sufficiently diverse to address various scenarios. This may require conducting analysis to identify any skewed or incomplete datasets.
Ensure human oversight
As AI-generated outputs can be incorrect, we’ve observed human oversight is necessary to verify outputs. This is particularly important in the context of decision-making. Given AI datasets may be biased, AI may misinterpret data in more nuanced scenarios, and the rationale for AIgenerated decisions can be opaque particularly if algorithms are proprietary.
Security awareness training
We strongly encourage the delivery of security awareness training to all users across an organisation to ensure they understand their responsibility when accessing systems and data. Additional training should be provided for users with elevated access and users who are tasked with specific security responsibilities, such as administrative users, security engineering teams and incident response teams.
Training should be provided upon onboarding and regularly thereafter to maintain awareness of security best practices as the threat environment and technologies continue to evolve. Incident response drills should also be conducted regularly to test responses to various incident scenarios.
Why CyberCX for Secure Cloud & AI
Using CyberCX for cloud transformation offers several advantages, especially for organisations aiming to ensure a secure and seamless transition.
Our dedicated Cloud Security and Solutions capability includes over 130 specialists who are experienced across the full end-to-end build and transition journey, focused on the intersection between cloud and security – architecture, engineering, operations, FinOps and governance.
Expertise and experience
With the advent of cloud technology and agile methodologies, there has been a cultural shift towards automation, scalability and immutable configuration. CyberCX’s Cloud Security and Solutions (CS2) practice helps customers design, build and manage secure cloud and data solutions.
Multi-cloud
CyberCX has established strong partnerships with Amazon Web Services (AWS), Microsoft, Google Cloud, and hybrid VMware on all platforms to deliver top-of-the-range outcomes.
Security
CyberCX provides security assurance by design, combining cloud transformation and security to mitigate risk and ensure that best practice is applied at all levels. We accomplish this at service inception by formalising account design, automating and orchestrating security control configuration, and aligning to regulatory controls relevant to your industry.
Trusted partner
CyberCX is a trusted partner to Australia and New Zealand’s most well-known commercial organisations as well as large government agencies. We are one of a handful of officially recognised AWS Security Competency and Microsoft Advanced Specialised partners.
Customised
Our team specialises in tailoring cloud security and transformation solutions to meet the specific client and operational needs.
Accredited and certified
Our team combines our skills, experience and expertise across the entire cloud portfolio to help mitigate risks, reduce costs, and provide time to meet business objectives.
Continuous monitoring and incident response
By leveraging the expertise of CyberCX, organisations can achieve a secure and efficient cloud transformation, minimising risks and ensuring compliance. Our team can design and implement automated solutions to monitor IaaS and SaaS security in real-time, providing alerts and automating remediation for vulnerabilities and misconfigurations.
Our cloud operations and security teams also provide several cloud managed services for AWS and Microsoft, Cloud FinOps, security monitoring and managed remediation services.
Advanced security measures
Our CS2 practice helps customers design, build and manage secure cloud and data solutions through the services listed below.
Cloud transformation
- Cloud migration and application modernisation
- Cloud landing zones
- Cloud security protection
- Data analytics and governance in the cloud
- Shadow IT
Management of the cloud
- Managed services for Azure
- Managed services for AWS
- Cloud FinOps services
- Continuous monitoring
Risk, compliance and regulatory support
Our CS2 practice also provides several advisory services including cloud strategy, governance and security through the following services.
Cloud security assessments
- Australian Cyber Security Centre security assessment services (IRAP)
- Technical cloud security assurance services
- Well Architecture Reviews
- Essential Eight (technical) assessments
- Copilot assessments
Cloud governance, risk and compliance
- Cloud governance framework
- Cloud architecture advisory
- Security Risk Management Plans
Cloud security advisory
- Cloud strategy and roadmap
- National Security and Defence advisory services
- Cloud DevSecOps advisory
- Operating model and implementation roadmap
Cloud and AI capabilities
CyberCX recognises that hyperscaler cloud solutions designed for the general public may not meet the security risk appetite of organisations with sensitive data requirements. These solutions can lack the sovereignty, security controls and governance required to support critical operations securely. This has left sectors such as defence and government, healthcare, and academia with a cyber maturity gap, exposing them to undue risk.
To mitigate this gap, CyberCX has developed the following platforms to enable organisations to rapidly adopt secure cloud and AI solutions.

Sovereign cloud platform
CyberCX partnered with Curtin University to develop Nebula, a sovereign cloud platform purpose-built to meet the Australian Government’s Information Security Manual PROTECTED standard.
The key features of the Nebula cloud platform include:
- Set up in weeks: Your secure Nebula environment can be configured and operational within weeks.
- Safeguard sensitive data: Meet the stringent PROTECTED classification, including 24×7 monitoring to protect your organisation’s data.
- Safely test and use AI: Take advantage of the latest tech in a secure environment to boost innovation.
- Support collaboration: Keep strong safeguards while collaborating easily with internal and external teams.
- Improve ongoing security: Provides an ongoing response to evolving cyber threats with proactive threat management.

CyberCX GenAI platform
CyberCX developed a GenAI platform for organisations to adopt AI in an accelerated manner. This platform utilises the security measures including data encryption and access controls to secure data.
The key features of the CyberCX GenAI platform include:
- Rapid implementation: GenAI solutions can be deployed in days with one-click deployment to production environments.
- Seamless connectivity: Connects with existing systems in cloud and on-prem such as data platforms, APIs, databases, file stores etc. This includes pre-built connectors for popular business applications for the use in RAG.
- Multi-agent support: With multi-agent GenAI systems becoming a standard in solving complex challenges, our platform provides all the necessary elements for building and operating such systems.
- Governance and control: Centralised model management and monitoring, as well as comprehensive audit trails and reporting.
Case Study: MyHR
Our Solution
Our Solution CyberCX supported MyHR with a comprehensive solution, in a two-phased approach:
Phase one: CyberCX Data Platform
A battle-tested accelerator solution – the CyberCX Data Platform – was used to consolidate MyHR’s disparate data sources, standardise data formats, establish governance controls and create a single source of truth for operational intelligence.
Phase two: CyberCX GenAI Platform
Based on the latest AWS services in GenAI, CyberCX built the platform with security, modularity, maintainability and cost- effectiveness at the forefront.
Using Bedrock Flow, CyberCX orchestrated complex workflows with multiple different Large Language Models (LLMs) invocations in a maintainable and extendable way.
A testing strategy was also implemented to allow individual components and the entire workflow to be tested, ensuring the solution is aligned with Responsible AI principles.
Context
MyHR built a SaaS platform, to make Human Resources (HR) straightforward and savvy. Their aspiration was to make HR work for every business where people are taken care of, and everyone can focus their energy on building success. MyHR now supports over 39,322 individual employment relationships in more than 1,680 businesses across New Zealand, Australia and Canada and has a strong further growth aspiration. MyHR was running a successful SaaS platform however, with increasing demand, their support team started facing increasing operational pressures due to repetitive, manual tasks that consumed valuable time and resources.
Outcomes and impact
The consolidation of data sources through the CyberCX Data platform, followed by the implementation of an advanced GenAI platform, enabled MyHR to achieve substantial gains in task automation and workflow efficiency without additional technical support effort, thanks to a secure, scalable, and maintainable solution built with rigorous DevSecOps and IaC practices.
With both platforms built based on AWS- native services, CyberCX was able to deliver a future-proof solution with the highest level of scalability, reliability and access to state-of- the-art LLMs.
Leveraging reusable, production-ready pattern templates designed and built by CyberCX also resulted in significant cost efficiencies for the engagement.
FAQs
What are the five key obstacles to secure cloud and AI adoption?
Through CyberCX’s extensive work assisting companies with cloud strategy, design, migration, and security, we have observed these five key obstacles:
- Increased business pressure to use AI across the IT environment
- Data security and privacy
- Complexity and skills shortage
- Identity and access management
- Growing privacy, regulatory and compliance requirements
By implementing robust security measures, continuous monitoring, and compliance with regulations, organisations can leverage the benefits of the cloud while minimising risks.
What are the best practices for building a secure cloud and AI environment?
Best practices include defining a clear cloud and AI strategy, establishing strong data governance, using defence-in-depth security architecture, adopting Zero Trust, applying encryption, segmenting networks, and implementing robust IAM and DLP controls.
How can organisations maintain security and performance in cloud environments over time?
Organisations should implement robust guardrails, perform continual optimisation and tuning of cloud resources, use Cloud Security Posture Management (CSPM) tools for real-time monitoring, and automate compliance checks to prevent misconfigurations and rising costs.
What processes strengthen threat detection and incident response in the cloud?
Key processes include using cloud-native monitoring tools, centralising security visibility, applying AI-based monitoring, ensuring access to provider logs, leveraging XSOAR for automated response, and implementing controls to mitigate insider threats.
Talk to a Cloud & AI Security Expert
Contact us to find out how CyberCX can help your organisation manage risk, respond to incidents, and build cyber resilience.