Our CORIE Story: Insights from the nation’s leading cyber intelligence-led exercises

Published by Cyber Intelligence 14 February 2024
Every year, multiple Australian financial services organisations undertake a CORIE – a Cyber Operational Resilience Intelligence-led Exercise – to test their cyber resilience. This approach reflects global best practice for critical infrastructure organisations. This blog explores the threat intelligence phase of the CORIE framework; a second in this series will examine the red team phase. It’s been written for financial services organisations getting “CORIE ready”, and all organisations looking to adopt the gold standard in intelligence-led operational resilience exercises.
In 2023, CyberCX Intelligence was honoured to win the lion’s share of Cyber Operational Resilience Intelligence-led Exercises (CORIE) in the Australian market. We had the privilege of helping top tier financial institutions better prepare themselves to face resolute cyber adversaries, testing the maturity and resilience of their business operations by simulating real-world attacks.
These exercises – an initiative by Australia’s Council of Financial Regulators (CFR) – were developed in line with similar frameworks globally, which have now become the de facto gold standard for assessing the cyber resilience of critical infrastructure organisations.
With threat intelligence at its heart, the CORIE framework sits in a class of its own, with no other framework offering the same rigour and results. Exercises are overseen end-to-end by the Reserve Bank of Australia (RBA), with the nation’s top cyber security agency, the Australian Cyber Security Centre (ACSC), reviewing, validating and endorsing the cyber intelligence assessments.
In this blog, part of a two-part series, we focus on the Attack Preparation phase of the CORIE process, which is entirely underpinned by threat intelligence. We share insights on how we conduct these exercises, and the threats we’ve found, to help all critical infrastructure organisations with their approach to cyber resilience.
Targeted reconnaissance
To simulate real-world cyber threats, we start all CORIE engagements with targeted reconnaissance, using the same techniques used by known threat actors. This includes discovering network infrastructure, uncovering corporate access entry points, information gathering on key personnel, scouring the deep and dark web for leaks, and identifying weaknesses in third-party supply chains.
Just like a motivated threat actor targeting an organisation, we leave no stone unturned. We amass data points and build a virtual picture of the organisation to identify weaknesses.

Illuminating the deep and dark web
A key part of our process is scouring cyber criminal forums and marketplaces, both open and closed. Our visibility into this illegal economy lets us see the evolution and ongoing commoditisation of cybercrime goods and services – from malware and credential bundles to network accesses. Initial access broker (IAB) marketplaces have become an indispensable part of this ecosystem, increasingly being used by cyber extortion criminals to buy access to their next victim.
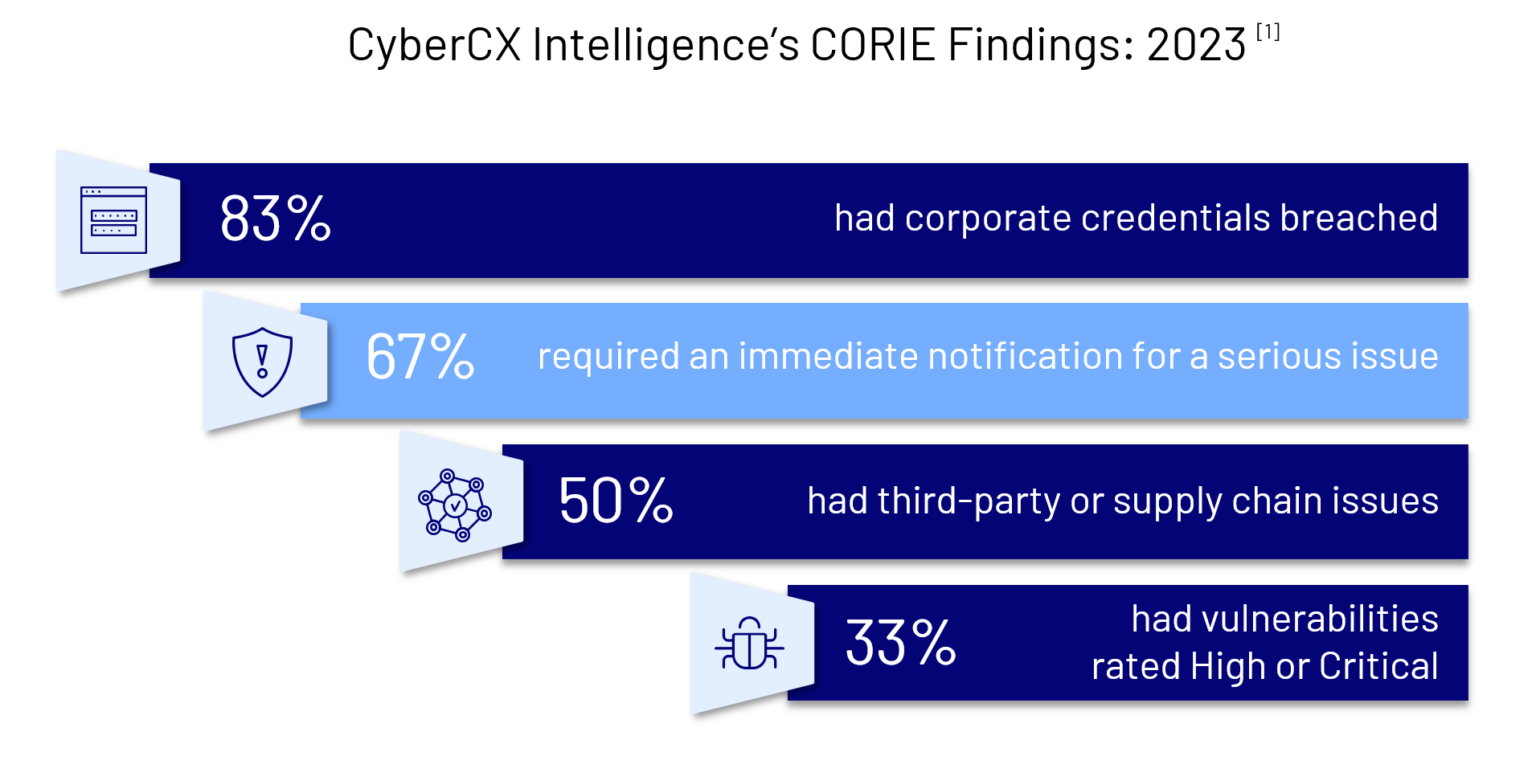
During our CORIE engagements, we consistently uncover sensitive information that requires us to “break the fourth wall” of the exercise. In fact, in more than 2 in 3 CORIE engagements, we needed to pause to immediately notify our customer about stolen corporate credentials.[1] And no, these weren’t your typical ‘combo lists’ of aged-out passwords; they were generally contractor or third-party consultant machines infected with ‘information stealing’ malware which had siphoned off sensitive credentials which had access to corporate resources.
The credentials Achilles’ heel
As part of our reconnaissance, we also dive deep into exposed corporate credentials. With such a large – and, unfortunately growing – body of historical Australian cyber security data breaches to trawl through, it’s rare that we don’t uncover a few corporate credentials. This is evidenced by our findings that 83% of participants had compromised accounts. However, as many security practitioners would say, data ages and the leaks become irrelevant.
Or do they? While we found past credential breaches that were no longer ‘active’, we also found multiple cases of users recycling their credentials with simple permutations – often a by-product of aggressive password expiry policies making users regularly, and unimaginatively, update them.
Network infrastructure
Network enumeration and attack surface discovery make up a large part of the Attack Preparation phase. Rather than dumping data points in a report, we place findings in context with operational or strategic intelligence. Are discovered vulnerabilities known to be exploited? By what type of threat actor and how? Are trust relationships in your supply chain a potential weakness?
Given that the financial services sector is heavily regulated and has above-average cyber maturity, it’s unusual to find critical or high vulnerabilities on infrastructure. This is reflected in our findings that only 1 in 3 participants had ‘high’ or ‘critical’ vulnerabilities to address. These weaknesses were generally in parts of the network that might have been decommissioned, were legacy, or part of testing infrastructure. These environments can often be blind spots, where hosts are deployed without the same production level of defensive controls. As is custom, where we found serious vulnerabilities, we notified participants immediately and gave them opportunity to remediate.
Threat scenario
The final stage of the Attack Preparation phase is building an intelligence-led threat scenario. Following the CORIE framework, we build a custom scenario for each participant based on their organisational profile and critical business services. The scenario is informed by latest geopolitical, cybercrime and threat actor trends.
To build the scenario, we select a real-world threat actor, based on our assessments of multiple threat actors’ intent and capability to target the participant and the way different attack types and tradecraft sets are likely to impact their critical business services.
It’s imperative that organisations test their security against real-world cyber threat actors and latest tradecraft — whether that’s nation-state actors becoming more efficient at evading Endpoint Detection and Response (EDR) tooling or highly capable extortion groups evolving their Tactics, Techniques and Procedures (TTPs).
Crucially, organisations will be most prepared if they adopt the mindset that a threat actor will breach some part of their network, and should seek to apply security strategies such as network segregation to curb lateral movement.

Passing the baton
At this point, we hand over to CyberCX’s Adversary Simulation Group, a highly talented team that specialises in exploit development and network intrusions. This signals the start of the Attack Execution phase in the CORIE process.
But the role for threat intelligence doesn’t end here. Engaging with CyberCX as both a threat intelligence and red team provider gives organisations the benefit of oversight of the CORIE process end-to-end. Our intelligence team is there to provide guidance and expertise throughout the Attack Execution phase, ensuring the integrity of the exercise and giving the CORIE participant the assurance that the engagement is truly intelligence-led.
[1] The statistics used in this blog post reflect CyberCX Intelligence’s experience conducting the threat intelligence phases of multiple official CORIE exercises in 2023 as well as “CORIE-aligned” exercises for Australian financial services organisations based on the CORIE framework.