A penetration test performed by a proven, certified cyber security company is one of the most powerful and effective ways to understand and improve your organisation’s security posture.
Whether you’re planning a new development project, are mindful of a potential upcoming compliance requirement, or are concerned about the brand damage a cyber security breach could cause, penetration testing gives you the confidence that your security practices are robust.
In this article, we answer the questions commonly asked by first-time penetration testing buyers and provide guidance to help you maximise the benefits of your penetration testing experience.
Here’s everything we’re going to cover (you can click the list below to skip to the relevant section):
- What is Penetration Testing?
- Why Invest in Penetration Testing & What is the ROI Value?
- What Role Does Penetration Testing Play in Cyber Security and Information Security Management?
- What Are The Different Types of Penetration Tests?
- What is The Penetration Testing Process & How Long Does it Take?
- How Much Does Penetration Testing Cost?
- How Often Should You Conduct Penetration Testing?
- How Do You Select a Penetration Testing Provider?
- What Are Some of the Common Pitfalls to Avoid When Hiring a Cyber Security Company?
- Get Started With Penetration Testing
What is penetration testing?
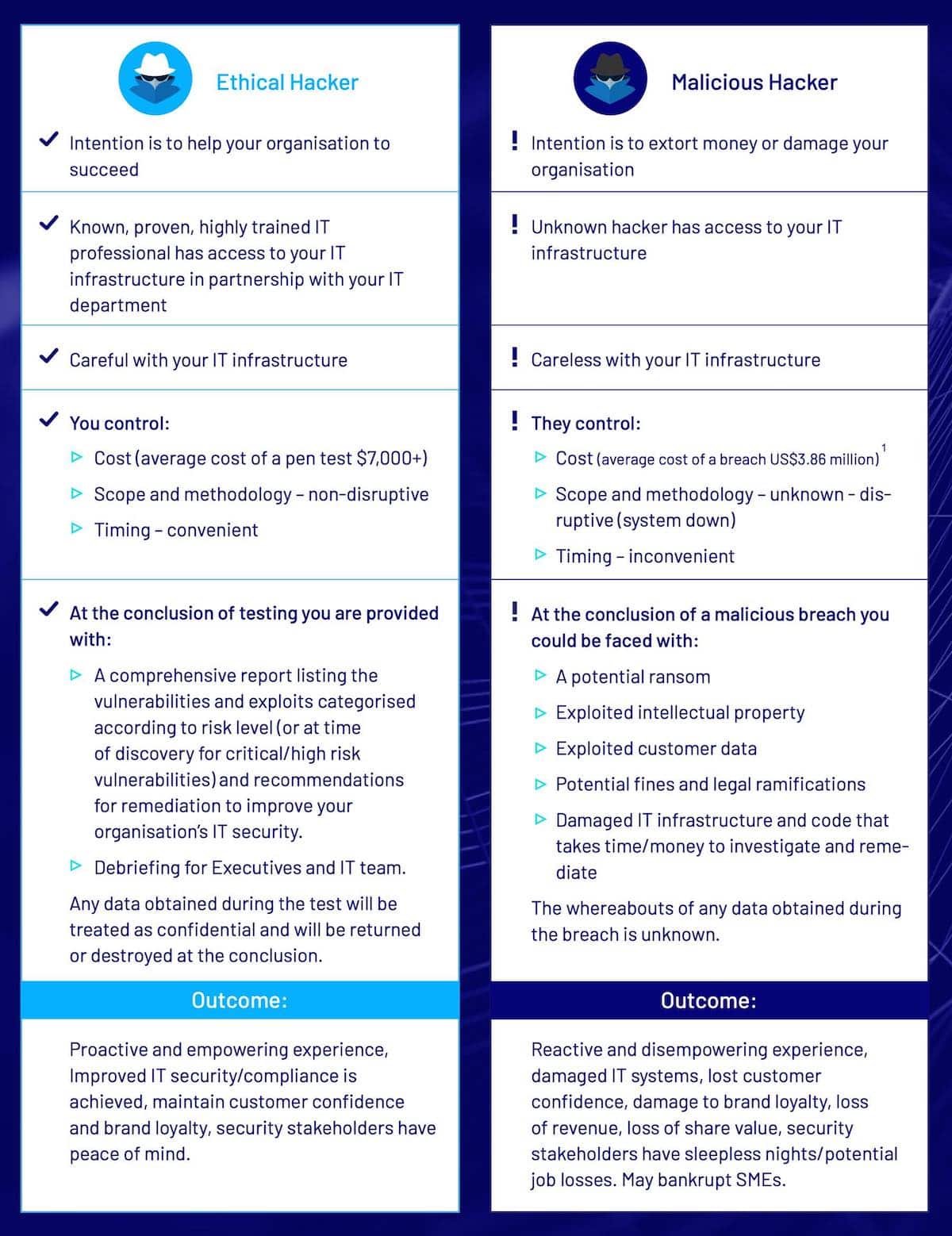
A Penetration Test (also known as ethical hacking or a pen test) is an authorised hacking attempt targeting your organisation’s IT network infrastructure, applications and employees.
The purpose of penetration tests are to strengthen your organisation’s security defences by identifying areas that are susceptible to compromise (vulnerable) and advising on remediation.
Why invest in penetration testing & what is the ROI value?
From the management team’s point of view, deciding to commit to an ongoing cyber security budget may be seen as adding yet another expense, with little visibility of a return on investment (ROI).
This can be particularly true for organisations not involved in the riskier areas of application development or ecommerce – perhaps they are a mid-sized manufacturing, transport or construction business – and think they’re not an attractive enough target for a cyber-criminal.
High-profile cyber security breaches regularly make national and even international news, often the result of a targeted malicious hacking attack. What is less well publicised are the more pervasive, lower profile breaches (often in-passing, opportunistic in nature), which are increasingly impacting small and medium-sized organisations.
This trend seems to be the result of the increased automation of cyber-attacks (targeting all and any); and the introduction of new vulnerabilities resulting from the adoption of new technology and working practices, including remote working and Bring Your Own Device (BYOD), such as laptops, tablets and phones.
In a rapidly changing technological landscape, organisations of all sizes must keep pace with not only the speed of innovation but also the resulting risks to information security.
Increasingly, organisations are incorporating cyber security into their overall risk management policy and business objectives into their security programs, with cyber security and information security management fast becoming the domain of management teams, not just the internal IT team.
These organisations recognise that cyber security and information security are, ultimately, just like any other risk they face in their business and therefore need to be managed like all those other risks, be they legal, operational, financial, etc. They understand not only that they can’t afford a ‘head in the sand approach, but that good security practices and compliance are a competitive advantage.
For organisations (predominantly SMEs), who are yet to adopt a more proactive approach to cyber security, complacency can be disastrous. With the increase in automated cyber-attacks, you can no longer hope cyber-criminals won’t take an interest in your business.
From February 2018, the amended Australian Privacy Act made the disclosure of cyber breaches to regulators and shareholders mandatory. The penalty for not doing so can be up to $1.8 million for organisations and, with additional fines of up to $360,000 for each board member, the message is clear; take cyber security seriously.
What role does penetration testing play in cyber security and information security management?
A penetration test provides your management team with an extremely fast and proven benchmark of the organisation’s level of risk, at a given moment in time, and prioritises the vulnerabilities found, in order of severity, with advice to expedite remediation.
This then provides your IT security team with the information they require to fast-track remediation work, demonstrates the ROI of existing security tools and facilitates the management team’s confident approval of security expenditure.
You can acquire this data in one of two ways, either proactively or via incident post-mortem and, put simply, investing in penetration testing is preferable to responding to a breach from a malicious hacker.
The decision of whether to invest in penetration testing is as simple as asking: “Do you want to choose your hacker?”
What are the different types of penetration tests?
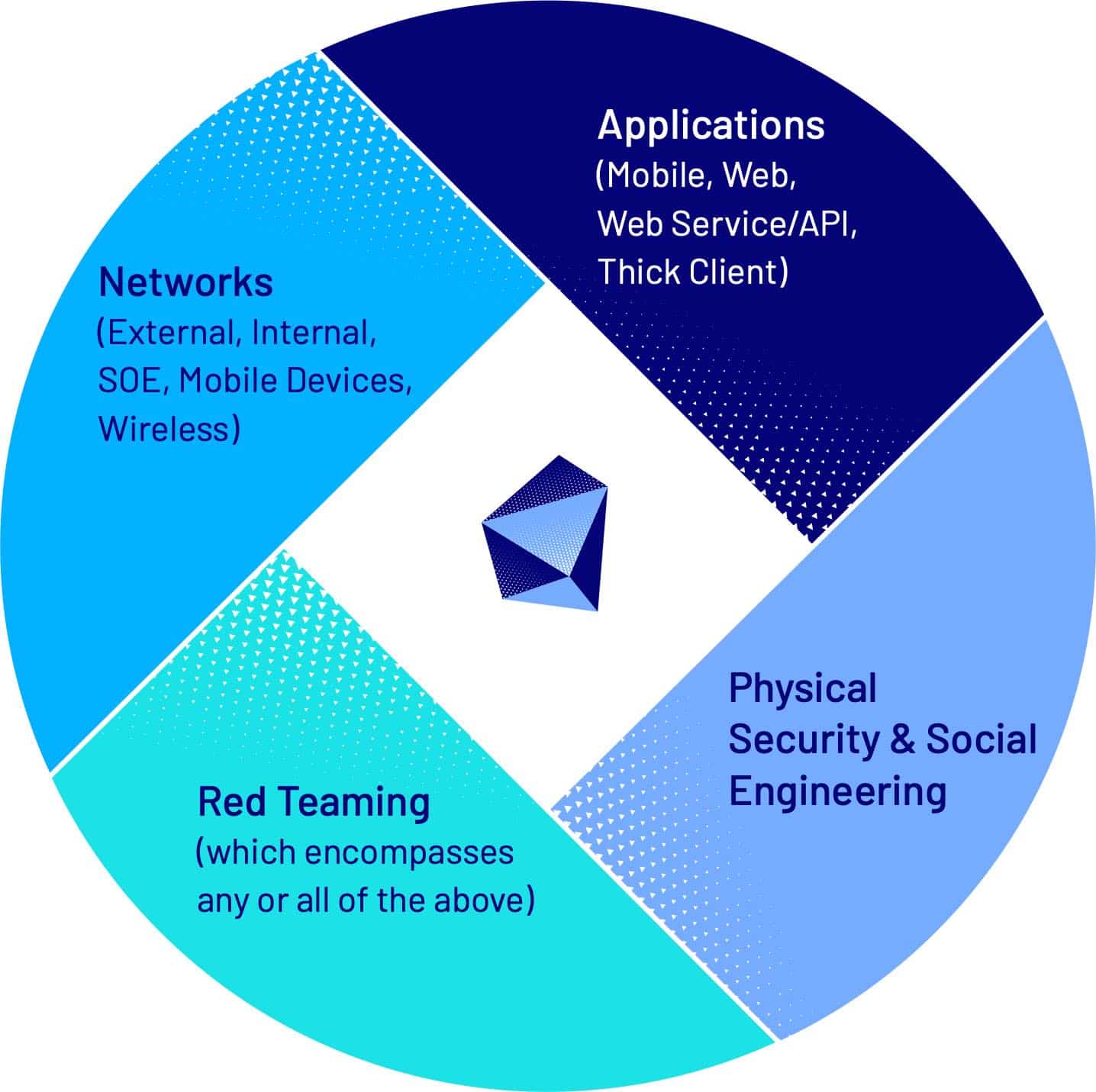
There are many types of penetration testing. They are generally categorised into:
- Network Penetration Testing
- Application Penetration Testing
- Physical Security & Social Engineering
- Red Teaming (which encompasses any or all of the above)
Application Penetration Testing
Best practice in application development considers information security from planning through development and all the way to production.
Unfortunately, tight deadlines often mean that security is left as an afterthought. This leaves applications vulnerable to cyberattacks that may compromise intellectual property and critical data.
Whether your application is live or in the development phase, penetration testing can help secure your applications.
Mobile Application Penetration Testing
Mobile App Penetration Testing is an authorised and simulated hacking attempt against a native mobile application (such as Android, Windows and iOS). The purpose of this test is to identify and exploit vulnerabilities in an application and the way it interacts and transfers data with backend systems.
Web Application Penetration Testing
Testing Untested Web applications remain the most common point of attack on an organisation.
Web application vulnerabilities have resulted in the theft of millions of credit cards and compromised sensitive information for organisations and end users.
A Web application penetration test targets open source and commercial software and custom web applications to identify and exploit vulnerabilities relating to authorisation, security configuration and data protection mechanisms.
API Penetration Testing (including Web Services)
An API penetration test aims to identify and exploit vulnerabilities in the architecture and configuration of an API and/or Web services. The purpose of this test is to identify ways you can fortify secure data exchange by demonstrating the ways a cyber-attack can compromise an API and/or Web service to gain access to an organisation’s information assets.
Thick Client Penetration Testing
A thick client penetration test identifies and exploits vulnerabilities in thick client applications.
Following an analysis of the application’s logic from both a static and dynamic viewpoint, testing includes a variety of tactics and techniques that cyber-criminals typically use to compromise a host or network.
Areas tested include client-side controls and protections, authentication issues, session management, access controls, input validation and handling, client to server communication and logic flaws, as each of these areas could indicate an avenue of exploitation.
Networks & Infrastructure
Networks are a lucrative target for cyber-criminals. A network penetration test helps you to identify vulnerabilities in your network assets such as external and internal facing servers, firewalls, routers and switches, remote access and VPN and wireless access points.
External Network Penetration Testing
An external network penetration test is an authorised hacking attempt against your organisation’s Internet-facing infrastructure, such as Web and email servers and ecommerce infrastructure.
This test aims to identify and demonstrate risks so you can harden your external facing network against attackers attempting to compromise vulnerable hosts from outside your organisation’s perimeter.
Internal Network Penetration Testing
Internal penetration testing aims to identify and exploit vulnerabilities from within your organisation’s perimeter defences.
For certain environments, such as data centres, dedicated testing machines are used to test remotely via your organisation’s VPN access. Alternatively, testers can be given on-site access (similar to the way employees or contractors could connect to an internal environment). They then attempt to escalate privileges and gain access to sensitive information.
Standard Operating Environment Penetration Testing
Standard Operating Environment (SOE) testing encompasses penetration testing of several different deployment types in which a standardised operating system image or hardened configuration is applied to a computer or virtual machine.
During SOE testing, testers apply attack scenarios relevant to the target platform, such as stolen devices and security policy bypass attacks.
Mobile Device Penetration Testing
Bring your own device (BYOD) has significantly increased the cyber-threat surface by creating a variable endpoint ecosystem.
The personal information accessed via employee mobile devices may be used for social engineering, allowing a cyber-criminal to gain a foothold into your organisation, and employee credentials may be used to attack the portal that the mobile device connects to and compromise sensitive information.
Mobile Device Penetration Testing attempts to bypass authentication on mobile devices including laptops, tablets and smartphones to assess whether stolen or lost devices can be compromised and then used as a pivot to compromise an organisation’s sensitive information. Testing can also assess third-party Mobile Device Management (MDM) implementations and devices configured with MDM policies.
Wireless Penetration Testing
An insecure Wi-Fi network opens your organisation to a myriad of attacks that could compromise your sensitive information. A Wireless Penetration test aims to detect and exploit vulnerabilities in security controls employed by a number of wireless technologies and standards, misconfigured access points and weak security protocols.
Physical & Social Engineering (including Phishing)
Investing in protecting your IT technology assets is meaningless if you do not also recognise the potential risks from social engineering and phishing.
Physical and social engineering penetration testing targets physical security controls and employee information security awareness to provide, often surprising, insights into areas requiring improvement.
Physical Penetration Testing
Physical penetration testing is the process of identifying and bypassing security controls implemented on buildings, data centres and employee operational security knowledge. All targets and exclusions follow specific pre-agreed criteria.
To prevent negative business impacts during testing, the following methods are generally used:
- tagging unsecured devices
- sending an email from unattended devices
- identifying and photographing exposed paper documents with sensitive information (in line with the client’s security standards).
Social Engineering Penetration Testing
Social engineering penetration testing replicates how cyber-criminals target employees to gain privileged access to protected systems and information by:
- Tailgating – the tester will attempt to follow employees into secure areas.
- Pretexting – the tester will impersonate an employee and attempt to persuade employees to divulge confidential information.
- Baiting – the tester will leave USB keys infected with malware inside and outside the building for employees to find and insert into a computer to replicate a USB Drop attack.
Phishing Attacks Risk Assessment & Penetration Testing
It takes only one user to fall prey to a phishing scam for an attacker to gain a foothold in your organisation. A phishing risk assessment and penetration testing service helps you to understand your organisation’s phishing posture and prepare for ransomware and other phishing-introduced threats.
Baseline Penetration Testing allows you to measure your organisation’s phishing risk. A simulated phishing campaign is sent to all end users or just a select control group. By tracking open and clickthrough rates, the campaign provides key stakeholders with a summary of the organisation’s phishing risk.
A more advanced Phishing Penetration Test also assesses the performance of the security stack at the desktop/server level and across the inbound and outbound points of the network. These technologies include file extension handling, port filtering, MIMES, type checking, anti-virus software, application whitelisting and proxy filtering.
Red Teaming
A red teaming assessment is the process of using all available resources (broad scope) to demonstrate the impact of a targeted cyber-attack. This can include identifying and bypassing security controls implemented on buildings, websites, servers, networks or by finding ways to abuse or bypass policy or processes implemented within an organisation.
By conducting this type of assessment, you can understand the effectiveness of current security controls and adherence to security policies and procedures in every way that they are exposed to threats.
During a red teaming assessment, testers will mimic the behaviours of a malicious hacker to understand what sort of vulnerabilities exist and what information they may be able to compromise.
Access more detailed information and guidance, including the benefits of each type of penetration test, here.
What’s the difference between a vulnerability assessment and a penetration test?
A vulnerability assessment is the process of identifying if an organisation’s systems / applications have potential known security vulnerabilities. It is an automated scan(s) followed by the generation of a report containing a prioritised list of the vulnerabilities found, the severity and generic remediation advice.
Scanning software is limited to identify only vulnerabilities it has signatures for (such as out-of-date software updates, incomplete deployment of security software etc). It cannot find vulnerabilities that are unknown. Scans include networks, web applications, source code and ASV for PCI DSS.
There has been some confusion around the role of vulnerability assessments, largely due to unscrupulous security vendors using low-quality scanning technology and producing poor quality reports (containing false positives and negatives) and little recommendation for remediation. To add insult to injury, they present (and price) their services as a penetration test.
This can give an organisation a false sense of security when in fact, they have only received a basic level of service.
Unlike a vulnerability scan, where identified vulnerabilities are not exploited, in a penetration test, the tester will modify their approach to provide proof of vulnerability through exploitation to gain access to the secure systems or stored sensitive information that a malicious attack could compromise.
In the hands of a certified cyber security professional, using industry leading vulnerability scanning technologies, vulnerability assessments are a useful resource; as a research tool during the reconnaissance phase of a penetration test, as a necessary component for achieving compliance or as part of an organisation’s ongoing vulnerability management plan.
The quality of the results is dependent on the quality/recency of the scanning software and the ability of the security professional interpreting the results.
A penetration test has much greater potential breadth of scope (e.g. social engineering) and depth than a vulnerability assessment. It should only be conducted by certified cyber security professionals who use their experience and technical abilities to mimic multiple types of attack used by a cyber-criminal, targeting both known and unknown vulnerabilities.
Unlike a vulnerability scan, where identified vulnerabilities are not exploited, in a penetration test, the tester will modify their approach to provide proof of vulnerability through exploitation to gain access to the secure systems or stored sensitive information that a malicious attack could compromise. The key characteristics of a vulnerability assessment and penetration test are compared in the table below.
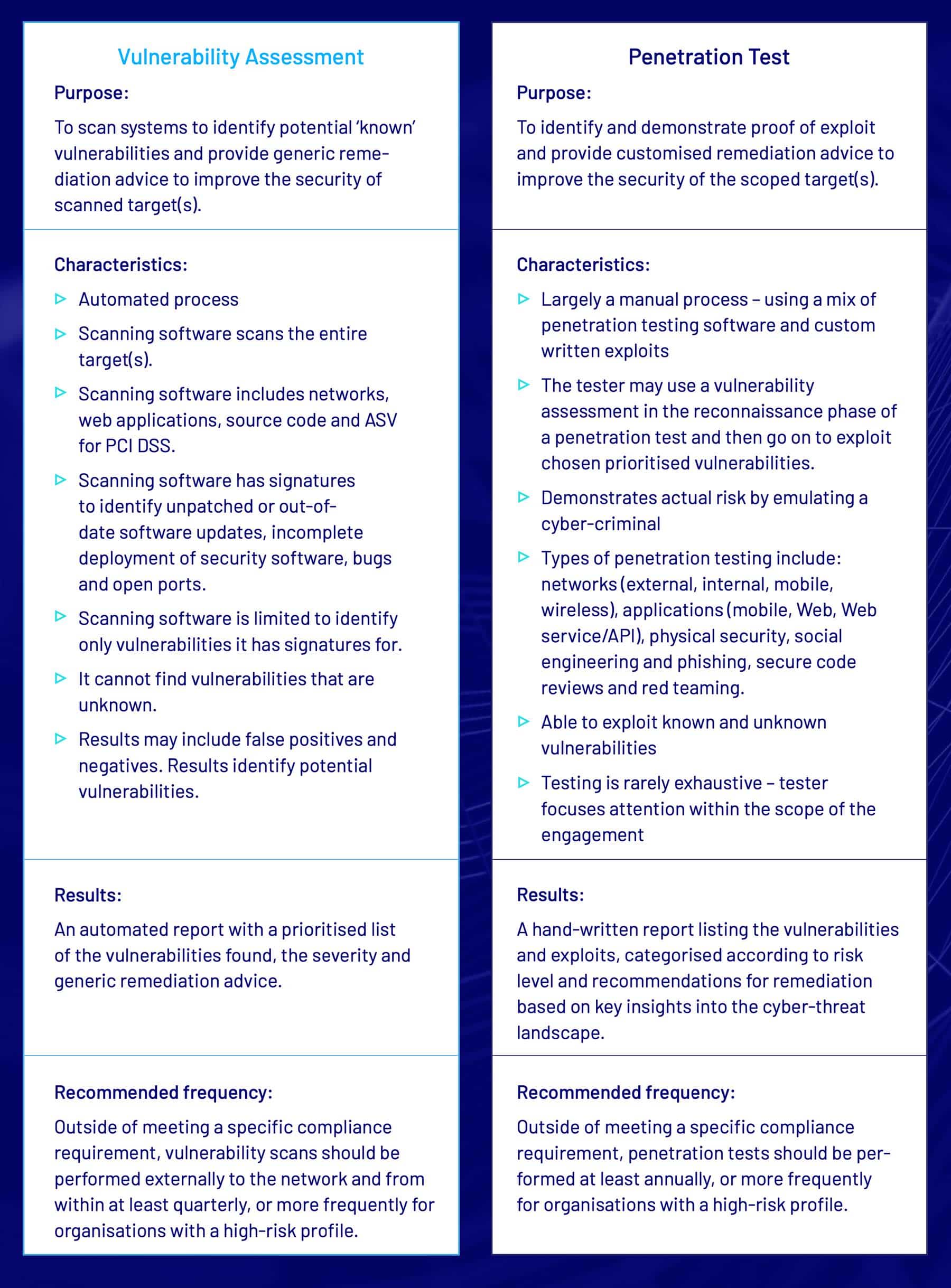
Together, a vulnerability assessment and penetration test enhance an organisation’s security posture. Both are essential components for achieving a strong cyber security and information security program – and a requirement for achieving and maintaining compliance.
Which approach: Black, White or Grey Box?
You will discuss the best approach to meet your organisation’s needs, with your penetration testing provider during the project scoping stage.
Your chosen provider will work with you to develop a customised test plan that will identify the objectives, scope, approach, limitations (e.g. avoidance of disruption of business operations) and legal and confidentiality requirements. Generally, the less mature an organisation’s cyber security and information security management program, the less aggressive and the more collaborative the approach. However, an organisation with a more mature program (and an identified high risk of cyber attack) may cycle between black box, grey box and white box approaches along with regular, ongoing vulnerability assessments.

Do you forewarn your IT team?
Another important consideration is whether the management team informs the IT security team about the date and scope of testing. While it is usual for all stakeholders to be informed, there are sometimes specific requirements not to do so, for example, in the case of social engineering penetration testing.
A red teaming exercise may use either approach. Borrowed from military terminology, the red team (penetration testing team) can attempt to exploit vulnerabilities either with the blue team’s (IT security team) prior knowledge and collaboration or without. Both methods provide valuable learning experiences for the blue team.
The decision of whether to inform the IT security team, in combination with the aforementioned approaches and testing methodologies, make up the general range of strategies employed to conduct a penetration test.
What is the penetration testing process & how long does it take?
There is no standard answer for the time it takes to conduct a penetration test, as it is dependent on the objectives, approach and the size and complexity of the environment (attack surface) to be tested – the scope of the work to be undertaken.
An app or small environment can be completed in a few days, but a large, complex environment can take weeks. A
reputable penetration testing provider understands the time constraints that face organisations and will have a process to deliver your penetration testing project as efficiently and cost effectively to provide maximum value.
Penetration testing generally has the following stages:
- Stage 1: Scoping
- Stage 2: Penetration Testing
- Stage 3: Retesting
- Stage 4: Remediation
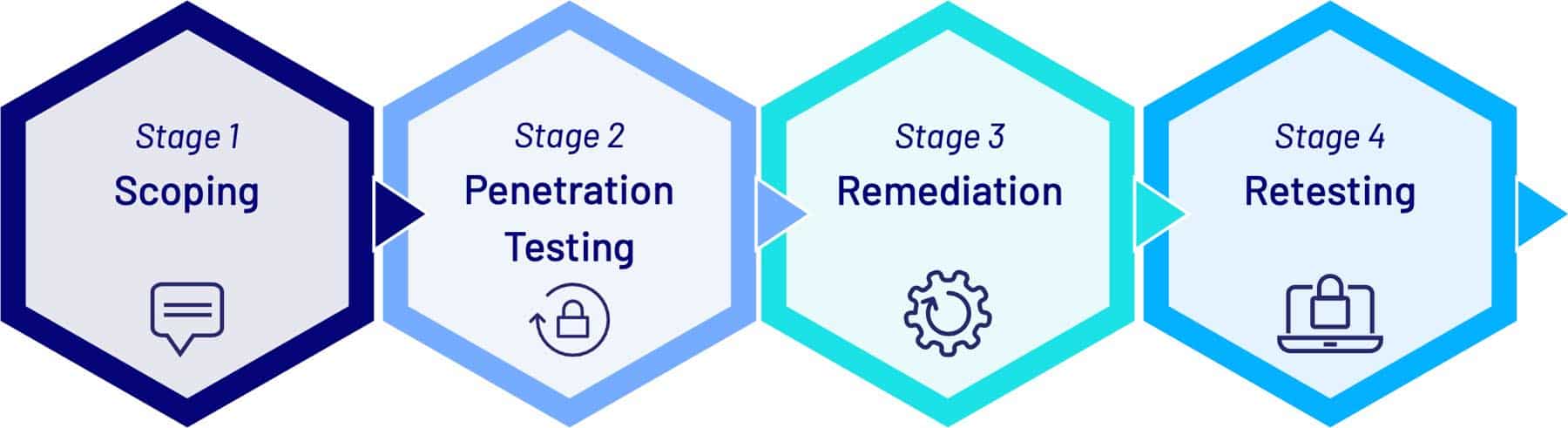
1. Scoping
An external network penetration test is an authorised hacking attempt against your organisation’s Internet facing infrastructure, such as Web and email servers and ecommerce infrastructure. This test aims to identify and demonstrate risks so you can harden your external facing network against attackers attempting to compromise vulnerable hosts from outside your organisation’s perimeter.
2. Penetration Testing
Reconnaissance and Analysis
Your penetration testing team will conduct a comprehensive reconnaissance against your organisation using various hacking techniques, within the parameters of your testing plan, to research potential vulnerabilities. They will then analyse and correlate the results to create a detailed picture of your organisation’s current security position – highlighting potential vulnerabilities. This will provide information critical for the testing and exploitation phase.
Testing and Exploitation
Your penetration testing team will launch carefully planned and calculated hacking attempts, within the parameters of your testing plan, targeting each potential vulnerability discovered during the reconnaissance phase. These attempts will use a variety of tactics and techniques at a level of threat equal to what malicious hackers would typically use. These proven tactics and techniques, at realistic levels of threat, will produce the most valuable output for your organisation. During this phase, the testing team will provide regular progress updates and any critical or high-risk vulnerabilities will be reported at time of discovery, to allow for immediate remediation.
Post exploitation
On successful completion of the testing and exploitation phase, any changes to the infrastructure and network will be restored to the state prior to the commencement of the test. This will provide a known security baseline for your organisation. Your penetration testing team’s methodologies should be planned and scheduled to be non-disruptive to ensure uptime throughout testing.
Reporting and Analysis
After completion of the testing phase, your penetration testing provider will issue a thorough report listing the vulnerabilities and exploits, categorised according to risk level, and recommendations for remediation based on key insights into the cyber-threat landscape. A good quality provider will also conduct debriefing sessions targeting two separate audiences: A technical debriefing aimed at system administrators and engineers. The technical briefing is intended for knowledge transfer – of the lessons learned during the penetration test – to the IT security team. An executive debriefing tailored for the technology management group. This session provides the information needed to determine the appropriate risk management strategy.
3. Remediation
Your IT security team will remediate the vulnerabilities, in order of severity. Many penetration testing providers also offer additional services, such as managed services, consulting and training for IT professionals, which may help your organisation to reach its security objectives more quickly.
4. Retesting
The scope of your penetration test may include a retest or it can be added within 45 days of the conclusion of the original penetration test. A retest only tests the vulnerabilities identified in the penetration test and is therefore quicker and costs less than the original test. Retesting may be required to achieve compliance. Outside of compliance testing, a certificate of completion can be provided where no critical or high-level vulnerabilities are found.
How much does penetration testing cost?
There is no universal price for a penetration test. In fact, if you are presented with a generic price it should serve as a red flag not to proceed with that provider.
A good quality penetration testing provider will provide a free consultation to understand your organisation’s aims and objectives and determine a high-level threat model (to understand the full scope of work) before they provide a quote.
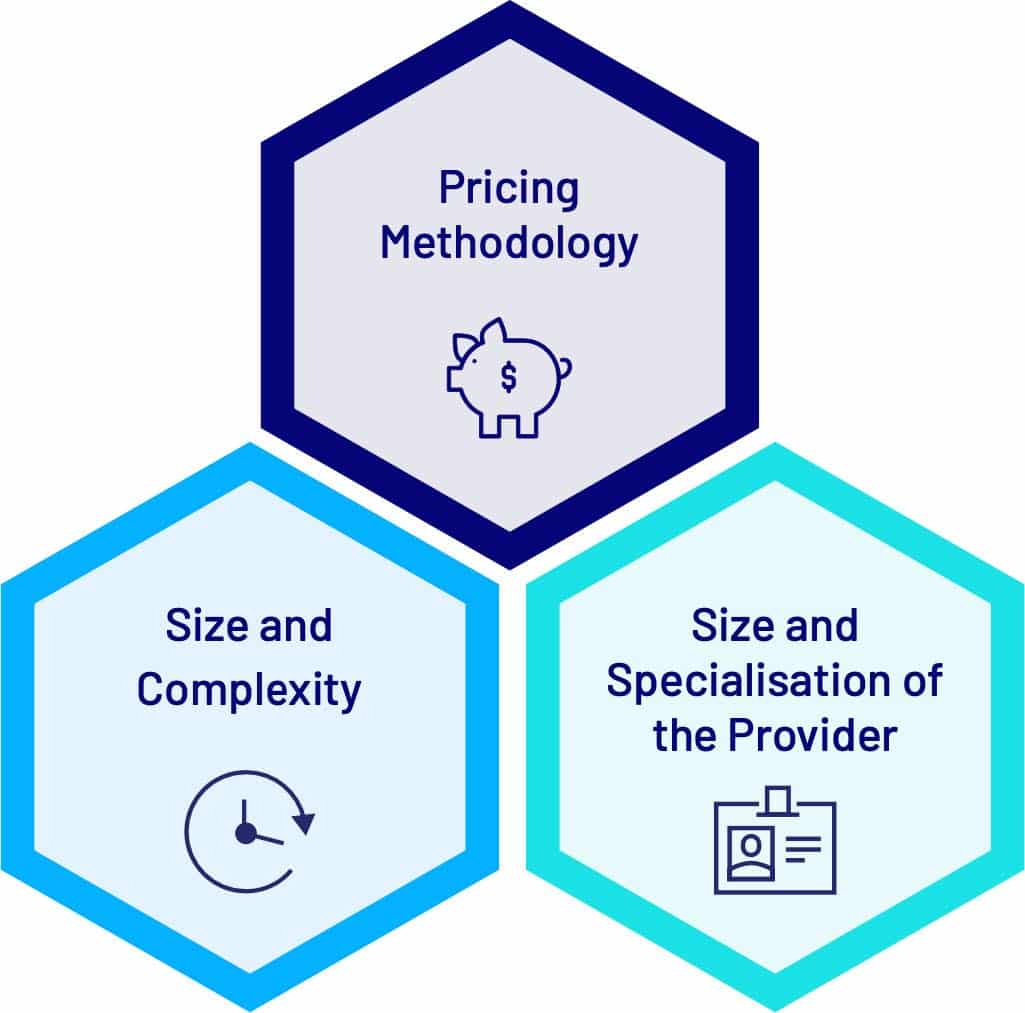
What can affect the price of a penetration test?
The following common variables will affect the cost of penetration testing services:
- Pricing Methodology
- Size and Complexity
- Size and Specialisation of the Provider
Target count vs measuring the attack surface
The approach and tools used will affect the price of a penetration test.
The most accurate pricing methodology, offering the best ROI for clients, is to measure the attack surface – the sum of potential attack vectors (any parameter that can be attacked) in the environment/app to be tested.
This approach ensures that sufficient time is allocated to focus on each attack vector and will deliver comprehensive results for the best value.
A target-count pricing methodology (price per IP address or price per page/click) can only provide a rough order of magnitude and shouldn’t be relied upon in isolation or it will likely result in a poorer ROI; with clients potentially overpaying on targets with no/a low attack surface and/or penetration testing providers relying heavily on automated vulnerability scanning on occasions where they find they have underquoted.
Size and complexity of the project
The size and complexity of the attack surface will be calculated and translated into number of hours/days/weeks of work. The larger and more complex a project, the higher the cost. This takes into consideration any special requirements, e.g. testing outside of normal working hours, onsite, in a production environment and on third-party infrastructure, e.g. cloud services.
Size and specialisation of the penetration testing provider
Clients may aim to ensure the quality of their penetration testing services by engaging large cyber security consultancies or their regular large IT outsourced partner, who has a penetration testing offering. This can also be problematic.
Large consultancies tend to predominantly work with enterprise clients on complex projects attracting higher daily rates. If your organisation does not meet this profile – i.e. a SME with straightforward testing requirements – it may be more cost effective to source a provider who also services smaller organisations; or it could be akin to hiring a barrister to challenge a parking fine.
It is also best practice to engage a provider who is independent from your day-to-day IT operations staff/providers who can look at your organisation’s IT environment from an outsider’s perspective.
At the other end of the scale, a low quoted price may be indicative of a lack of industry accreditation. The cyber security industry has defined minimum standards for providers who have the capability and skills to conduct penetration testing activities.
The key requirement for assessing a provider’s capability is the CREST designation. If the provider is not a CREST accredited penetration testing firm, they have not demonstrated the knowledge, skills and understanding to be trusted with your testing activities.
A certified provider that specialises in, and conducts numerous, penetration tests will have the most accurate scoping capabilities to provide you with the best balance of quality service at a competitive price. They will offer you a broad range of penetration testing services and have the latest tools and techniques, plus the ability to author their own custom tools – to give you the best value.
They will have numerous multi-certified, experienced penetration testing consultants with preapproved security and will have a process to deliver your penetration testing project as efficiently and cost effectively as possible. And this accumulated knowledge and experience will also provide you with a detailed penetration testing report with valuable insights into remediation actions.
How often should you conduct penetration testing?
Including regular penetration testing in your ongoing cyber security and information security management program is the best approach, after all, the cyber security landscape is ever evolving.
Compliance requirements mandate regular penetration testing – for example PCI DSS compliance requires penetration testing, at least annually or during infrastructure and application modifications and upgrades that constitute a significant change to the environment.
Often, organisations aim to meet only the minimum requirements to achieve compliance – and believe themselves to be secure. This is a dangerous mindset. The best practice approach is to work with your provider to conduct an organisation-wide risk assessment to determine your organisation’s level of risk. You can then develop a cyber security program that employs an agile approach, using the tools at your IT department’s disposal and your provider’s (such as vulnerability assessments and penetration testing) to measure and evolve the security of your networks, applications and employees to maintain a strong defence against cyber-attack.
There are many benefits to this approach, including:
- Ongoing, improved security
- Cybersecurity remains front-of-mind with all employees
- Better Return on Investment – smaller regular engagements
- Confidence in the IT budget and security spending
- Knowledge transfer in security best practice to your organisation’s IT security team and application code developers – reduced future remediation work
- Organisations can leverage good security practices (including any compliance) as a competitive advantage.
- Better placed to respond quickly to future changes in both compliance requirements and cyber threats.
- Better placed to successfully manage a security breach.
It is recommended that vulnerability assessments should be performed at least quarterly. If this is too great a commitment for your organisation, many providers offer ongoing vulnerability assessments as a managed service.
How do you select a penetration testing provider?
With a vast number of providers to choose from, it’s essential to do your research to ensure that your chosen penetration testing provider is proven, reliable and professional beyond reproach.
You will rely on them to interrogate your business systems and use complex tools to fully test your IT network. If the provider lacks knowledge and experience in applying their tools to diverse IT environments, you may waste your money and fail to see results. Worse, your IT environment could be damaged, changed or taken down if penetration testing tools are not appropriately configured for your specific environment.
Best practice penetration testing provider characteristics
For the best outcome, look for providers with the following characteristics:
1. They are a certified, specialist cyber security provider who is passionate about cyber security and conducts penetration testing as a core offering.
Your penetration testing team will conduct a comprehensive reconnaissance against your organisation using various hacking techniques, within the parameters of your testing plan, to research potential vulnerabilities. They will then analyse and correlate the results to create a detailed picture of your organisation’s current security position – highlighting potential vulnerabilities. This will provide information critical for the testing and exploitation phase. Have objective proof of capability, including recognised certifications such as CREST, SANS Institute (GPEN, GWAPT) and Offensive Security (OSCP, OSCE). Have extensive knowledge and experience and are at the leading edge of the latest security research, trends and attack vectors. Offer testing capability across all IT perimeters, including phishing.
2. They have a good reputation in the industry and a strong track record of value for money services.
3. They provide a free scoping and quote service
- Scoping research should measure the attack surface to provide a quote that offers their clients the best ROI.
4. They have a qualified and experienced penetration testing team
Testers:
- Have a deep understanding of multiple architectures and extensive experience in reverse engineering technology and how exploits work. They must be able to perform their own research and write their own code and exploits, if required.
- Are capable of testing in development and post-production environments.
- Already have the necessary security clearances.
- Can work on-site, if required.
5. They conduct a comprehensive penetration test
- Make sure it’s a comprehensive penetration test and not just a vulnerability assessment or a ‘tick-the-box’ compliance or audit exercise.
6. They deliver customised and practical reports and debriefing sessions with their clients.
- Reports are written by the tester, (not a software-driven canned report) are meaningful, helpful and customised to your environment.
- They provide a customised debrief tailored to both IT and management groups.
7. They are independent from your day-to-day IT operations staff/providers
It is best practice to use a provider with specialist skills who can look at your organisation’s IT environment from an outsider’s perspective.
How do I research penetration testing providers?
Before you sign on the dotted line, make sure you:
- Ask for proof of certifications
- Ask for references
- Review their service offerings (Look for a potential ongoing, trusted security partner with the capability to meet your organisation’s evolving cyber security needs)
- Ask for sample reports
- Ask who writes the report
- Ask for proof of testers’ qualifications and experience
- Ask for proof of testers’ police check and, if required, preapproved security clearance
- Ask if they are capable of testing in your environment(s) – development and post production
- Ask if they have experience in your type of network
- Check that testers are not outsourced or overseas
- Check that they are independent from your regular pool of IT providers.
- Ask about their scoping methodology
- Ask questions to ensure you understand the quote
What are some of the common pitfalls to avoid when hiring a cyber security company?
There are many common pitfalls that you can easily avoid by researching and selecting the right provider, having an information security mindset and not becoming complacent. Here are some tips to help you avoid common pitfalls:
1. Penetration Testing Pitfalls to Avoid
Many pitfalls can be avoided by taking the time to research and select a good provider. Pitfalls relating to providers include:
- Purchasing a penetration test that is a glorified vulnerability scan (you can run these yourself – for free!) and a report that is automated, contains many false positives and negatives and generic guidance.
- Paying for a methodology that charges for testing areas that do not require testing.
- The penetration tester is not adequately trained and damages your environment.
- The penetration tester does not have adequate security clearance – resulting in time lost while clearance is obtained.
- Engaging a large provider who has a pricing model aimed at the needs of enterprise clients, resulting in potentially high costs.
- Engaging your existing provider who is not a specialist in penetration testing, resulting in potentially higher costs and a poorer quality service than could have be achieved by engaging a provider that specialises in penetration testing.
- Engaging a ‘quick and low cost’ service to achieve basic compliance. You get what you pay for – your organisation may just meet compliance standards but have received a service that is insufficient for its level of risk.
2. Have an information security mindset
Having an information security mindset is important, not only for the IT security team and management team, but also every employee. The following pitfalls reflect how not having an information security mindset can be dangerous for your organisation.
Myth: “There is no need for a pen test – the IT department can find any holes in our security.”
- Your penetration tester should be an external, neutral party. The person finding the issues should not be the person responsible for fixing them as there will be blind spots and assumptions that will skew the results. Penetration testing will likely reveal problems your IT department didn’t know existed.
Myth: “Security was taken care of when the provider installed the system.”
- A ‘set and forget’ approach cannot apply to cyber security and information security management. Cyber security threats are continually evolving and have multiple points of attack and if your organisation does not keep pace with the level of threat, it is at increased risk.
Myth: “The security team don’t collaborate with the development team (and vice versa) and neither will partner with the pen testing team.”
- To effectively remediate security issues and prevent future issues, there needs to be a collaboration between IT teams throughout any development and penetration testing process. Egos aside, a collaborative approach is essential to achieve ongoing security.
3. Avoid becoming complacent
It’s important not to become complacent. Achieving best-practice cyber security and information security management is an ongoing and evolving process.
Myth: “My organisation has done a penetration test, therefore it’s secure.”
- The purpose of a penetration test is to help identify vulnerabilities and suggest remediation. It’s up to you to implement the remediation and commit to maintaining security – such as adding ongoing cyber security and information security activities to your organisation’s security management program. And unless the scope was for an end-to-end penetration test, covering the entire attack surface, the test may have focused on targeted areas only.
Myth: “My organisation is compliant, therefore it’s secure.”
- If your organisation takes a proactive approach to cyber security and information security threats and employs measures to meet your organisation’s level of risk, it’s likely that it is well protected – and compliant. If, however, your approach is to just meet the basic requirements to achieve compliance, your organisation may be compliant yet at a high risk of compromise.
Myth: “My organisation has so much testing that the network is bulletproof.”
- No network is bulletproof! Your understanding of penetration testing as a point in time assessment and commitment to reduce your risk with regular penetration tests will certainly improve the security of your network. However, investing in protecting your IT technology assets is meaningless if you do not also recognise the potential risk from social engineering and phishing, which is designed to circumvent your external network. Education must include not only the security team (system admins, database admins, developers) but all employees. Regular penetration testing that includes social engineering will help to identify and benchmark risk, and an ongoing phishing training program can provide your organisation with an ongoing, cost-effective solution.
Get started with Penetration Testing
Now that you know all about penetration testing, the ROI to organisations and how to choose a cyber security company to do your pen testing, you now have the knowledge and tools to make an informed decision.
By using penetration testing to keep your network and applications secure, we can all help to make Australia a harder cyber security target for cybercriminals.