
There’s no shortage of cyber news making the headlines, but what does it mean for you?
At CyberCX, we keep a close eye on the news to identify reports of the latest trends, issues and exploits.
Here we present a selection of recent news stories that caught our attention, and the important lessons we can learn to keep secure.
Delayed Reporting of Breaches Due to System Faults
System faults occur due to a business or technology process error. Whilst they only account for a minority of all notifications under the Notifiable Data Breach (NDB) scheme, they disproportionately go unidentified and unreported for long periods of time.
According to the latest report from the Office of the Australian Information Commissioner (OAIC), system faults cause 5% of breaches, considerably less than either malicious or criminal attack (65%) or human error (30%). Despite this, there tend to be considerable delays in reporting breaches due to system faults to the OAIC. In fact, 30% of breaches due to system faults are reported to the OAIC more than a year after the breach.
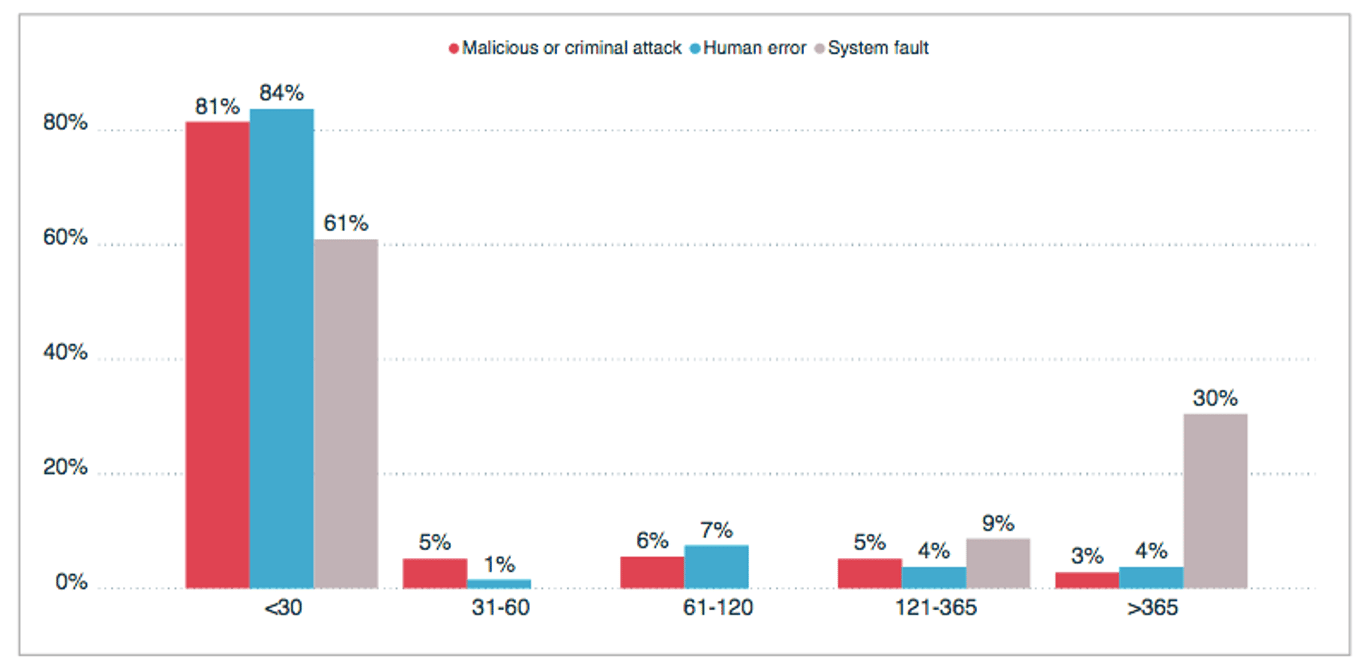
This delay in identifying and reporting system fault breaches is a cause for concern as a key objective of the NDB scheme is to ensure that an entity that experiences a data breach provides timely notification, ideally within 30 days, to individuals at risk of serious harm from the breach. Delays in assessment and notification reduce the opportunity for an individual to take steps to prevent harm.
It highlights the fact that an organisation’s processes are not ‘set-and-forget.’ There is a need for all organisations to regularly review and update their business and technology processes to ensure they are fit for purpose. Ideally, such reviews should be undertaken annually and would benefit from external expertise to independently assess the efficacy of all relevant processes, particularly as they pertain to an organisation’s responsibilities under the NDB scheme.
Cyber Criminals Target GitHub Repositories
ShinyHunters, a notorious cyber criminal group that’s been responsible for numerous data breaches since last year, has been observed searching companies’ GitHub repository source code for vulnerabilities and credentials.
The group has a history of compromising developer code repositories, such as GitHub, to steal credentials or API keys to a company’s cloud services. These are subsequently used to gain access to databases and gather sensitive information to be resold for profit or published for free on hacker forums.
Researchers claim that the group has exposed more than 1.12 million unique email addresses belonging to S&P 100 organisations, education, government and military entities as of late 2020. It is estimated that approximately 20% of all breaches occur as a result of compromised credentials.
Whilst ShinyHunters may not have the notoriety of other ransomware groups, monitoring malicious actors operating in repositories is crucial to preventing an organisation being compromised. It is thought that last year’s SolarWinds winds breach may have stemmed from credentials being inadvertently left in code that was stored in an open source repository.
This is an important reminder to all code developers to ensure that all credentials are removed from any code before storing it in any repositories such as GitHub. Having independent source code reviews throughout the software development cycle can help ensure such information remain confidential.
This is an important reminder to all code developers to ensure that all credentials are removed from any code before storing it in any repositories such as GitHub. Having independent source code reviews throughout the software development cycle can help ensure such information remain confidential.
Top API Vulnerabilities
APIs have become indispensable business tools for many organisations who rely on them to connect multiple applications. Due to the fact that APIs enable large volumes of data transmission, they have long been an attractive target for attackers.
Without proper security testing, APIs can become a perfect point of attack. Due to the fact they are trusted by an application, APIs should be a cause for concern for all organisations that are utilising them.
Researchers have identified the following three common API vulnerabilities all organisations should be addressing:
- Broken Object Level Authorisation (BOLA) which allows an attacker to perform an unauthorised action by reusing an access token.
- Broken User Authentication which allows attackers to impersonate legitimate users.
- Improper Assets Management which allows attackers to access under-secured API endpoints.
Ensuring the applications in your environment are not vulnerable to these three possible API bugs is critical. With expert API penetration testing, your organisation will be able to test the APIs connecting your applications to ensure they are not open to exploitation which can result in large-scale data breaches.
Microsoft Exchange Server Vulnerabilities
The Australian Cyber Security Centre (ACSC) is warning that threat actors are actively exploiting vulnerabilities in Microsoft Exchange Servers. These current vulnerabilities are separate from the ProxyLogon ones identified in March.
Of particular concern are the following three ProxyShell flaws:
- CVE-2021-34473 provides a mechanism for pre-authentication remote code execution, enabling malicious actors to remotely execute code on an affected system.
- CVE-2021-34523 enables malicious actors to execute arbitrary code post-authentication on Microsoft Exchange servers due to a flaw in the PowerShell service not properly validating access tokens.
- CVE-2021-31207 enables post-authentication malicious actors to execute arbitrary code in the context of SYSTEM and write arbitrary files.
According to researchers, attackers are chaining these three vulnerabilities together to perform unauthenticated remote code execution, and they only need access to the public-facing Web service of Microsoft Exchange, hosted on port 443.
These vulnerabilities are publicly exposed and accessible to anyone on the Internet, meaning attackers can scan the Web looking for vulnerable Exchange Servers. Microsoft has released patches for all three vulnerabilities. It is essential that all organisations ensure their patching is up to date.







