GoAnywhere: Another Cl0p global mass exploitation

Welcome to the March edition of Cyber Adviser, a monthly readout of insights and expert analysis from the CyberCX Intelligence desk.
Last month by the numbers
GoAnywhere: Another Cl0p global mass exploitation
In February, security researchers identified active exploitation of Fortra’s GoAnywhere MFT using a zero-day vulnerability, CVE-2023-0669. Following the release of a patch, the Cl0p cyber extortion gang claimed they’d used the flaw to steal data from 130 companies. Cl0p is a ‘Big Game Hunting’ actor that has been active since at least 2019. GoAnywhere MFT is a secure file transfer product provided by Fortra (formerly Help Systems).
Since February, Cl0p has been adding an increasing number of victims to its dedicated leak site (DLS). Cl0p’s March victimology represents a more than tenfold increase in activity rate relative to the trend over the previous 12 months.
Cl0p activity rate by victims listed to DLS per month from January 2022 to 26 March 2023.
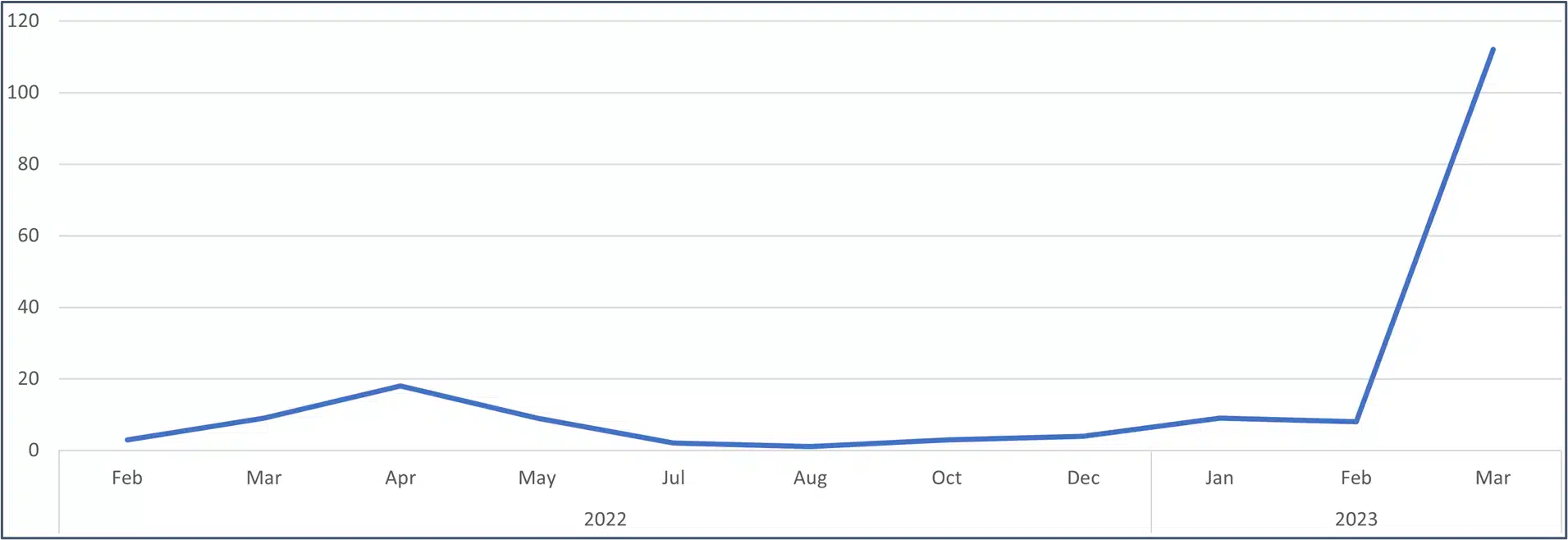
Cl0p’s campaign likely comprised rapid, superficial intrusions to exfiltrate enough data to attempt extortion, but with limited network penetration. Ordinarily, Cl0p pursues a ‘double extortion’ strategy, both encrypting data and stealing information. In this campaign, Cl0p hasn’t deployed ransomware against each victim, a decision we assess comes down to personnel limitations. Cl0p’s activity rate through 2022 is indicative of a small group that would have been unable to move laterally and escalate privileges in dozens of organisations concurrently. We assess that Cl0p is unlikely to operate under a ransomware-as-a-service model and is instead a traditional criminal gang.
Cl0p previously conducted a similar widespread campaign based on a single vulnerability in 2020, targeting vulnerable Accellion FTA systems. That campaign affected over 100 organisations, including a significant impact on New South Wales government agencies.
Resilient and adaptable: Threat actors shift to OneNote for malware delivery
Following Microsoft’s disabling of internet derived macros by default in mid-2022, threat actors have explored new techniques to distribute malicious attachments. From late December onwards, CyberCX has observed threat actors shift towards distributing malicious Microsoft OneNote files to infect victims.
OneNote allows embedded attachments to launch when double-clicked by a user, offering macro-like execution with low victim interaction. OneNote files can also be customised with images laid over attachments. Threat actors overlaid images masquerading as buttons over attachment icons to misdirect users about what they were clicking.
CyberCX is aware of malware delivery campaigns featuring Emotet and Qakbot using malicious OneNote documents since January 2023. It is also highly likely that North Korean nation-state actors are adopting the technique. Attacks leverage several different infection chains, suggesting that threat actors are altering their approach based on successes in infecting new systems.
Medusa Team, a new prolific cyber extortion threat
In February, CyberCX observed Medusa Team using a recently created DLS to claim compromises of at least 14 organisations, including one Australian organisation.
The Medusa Team cyber extortion group commenced double extortion operations in January. We assess that Medusa Team’s activity is distinct from other existing threat actors with similar names, including Medusa Locker, the Medusa Stealer botnet and the Medusa Android trojan.
Medusa Team’s DLS links to the online persona “OSINT without borders”. OSINT without borders operates a purported threat intelligence website and is active on criminal forums, impersonating a security researcher. We assess with high confidence that OSINT without borders is operating public relations and advertising functions for Medusa Team. Tactics associated with posts, including publicly disclosing breaches and reproducing data on the clear web, are likely seeking to amplify damage to victims.
You can read more about Medusa Team’s tradecraft and operations in our recent threat advisory.
OSINT Without Borders maintains an active social media presence.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely Australia and New Zealand focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. Our intelligence leverages CyberCX’s significant operational and advisory experience including:
- Case files from incident responses managed by our Digital Forensics and Incident Response practice, the largest DFIR team in the region.
- Telemetry collected by our Managed Security Services practice across 100+ Australian and New Zealand client networks.
- Insights collected by our Security, Testing and Assurance practice across 3,000+ penetration tests annually.




