September 2023

Your monthly readout of the Australia and New Zealand cyber threat environment from the desk of CyberCX Intelligence. Cyber Adviser cuts through the noise – delivering you insights and expert analysis in 5 minutes or less.
By the numbers
Case files
Could you prove a negative? When a breach isn’t a breach
In mid-August, the NoEscape cyber extortion group misidentified one of their victims as auDA, the .au domain administrator. An auDA investigation found no evidence of a breach or exposure of auDA-owned data. NoEscape had highly likely breached another entity and stolen data that merely referenced auDA. After auDA publicly disputed the claim, NoEscape reduced the negotiation timeframe from 8 to 3 days and released screenshots of alleged sample data, likely to increase pressure on auDA to pay the ransom.
CyberCX Intelligence is aware that cybercrime groups have misidentified their Australian victims on at least three occasions in the last six months. When victims are misidentified, stakeholders still expect transparent and timely updates, often before an investigation is finalised. Proving – and communicating about – a negative can be difficult. Organisations should ensure their playbooks for incident response, crisis communications and stakeholder management contemplate a scenario where a threat actor incorrectly claims – mistakenly or deliberately – to have hacked them.
Ransomware rising: With data confidentiality in the spotlight, don’t lose sight of the disruption risk
In early August, an operator of 16 hospitals in the United States was impacted by a cyber extortion attack. The attack, by ransomware-as-a-service group Rhysida caused service disruptions for a week, and several patients were diverted to other sites for medical treatment. Rhysida emerged in May, gaining notoriety for ‘double extortion’ operations against education, healthcare, enterprise and government organisations globally. In August, Rhysida claimed to have compromised an Australian healthcare organisation.
Following a string of recent, high-profile breaches in Australia, cyber teams and Boards are increasingly worried about the confidentiality of their systems and data. Rhysida’s operations are a reminder of the significant impact that attacks on availability can have, especially for organisations in front-line critical services. Previously, several ransomware-as-a-service operators self-imposed bans on targeting healthcare and government; but as fewer victims globally pay ransoms, groups like Rhysida are backing away from this approach.
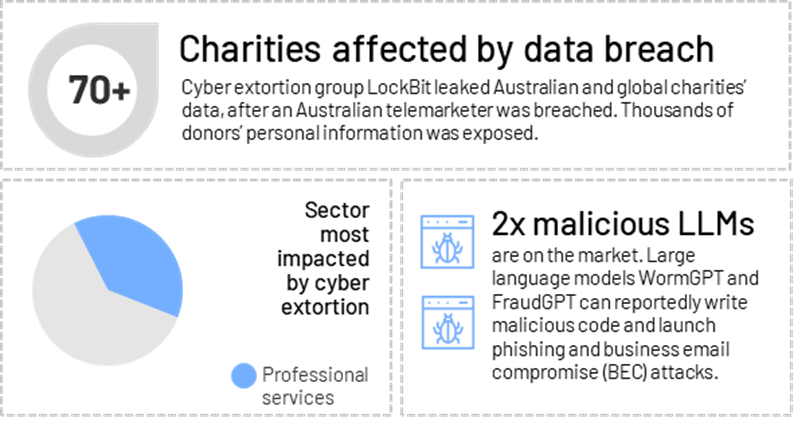
Data, the new uranium? Breach of charities’ information keeps attention on third party risk
In early August, a third-party data breach compromised the personally identifiable information of thousands of donors to over 70 Australian and international charities. The data, held by Australian telemarketer, was released on the darknet Dedicated Leak Site (DLS) of the LockBit cyber extortion group. The latest breach will continue to put pressure on impending privacy law reform to clarify responsibilities across the full data lifecycle, from collection to retention policies, and possible new consumer rights, such as a right to data erasure.
Locked bits or no bits? Trouble in criminal paradise
LockBit continues to be one of the most prolific cyber extortion actors in Australia and New Zealand, responsible for 1 in 5 claimed attacks last month. But there is some good news. CyberCX Intelligence is aware of multiple occasions where LockBit has published a victim name and claimed to have released victim data, but the data is not anywhere on the LockBit DLS. In fact, we assess that around 25% of organisations will not be impacted, or fully impacted, by data disclosure if they refuse to pay a ransom to LockBit. Organisations may wish to factor this into their incident response decision-making processes. However, here’s where the good news ends. Reputation is core to the value proposition that ransomware-as-a-service organisations offer their affiliates – LockBit’s data leaking woes are likely to drive criminals to other cyber extortion groups. CyberCX has also observed affiliates breaking LockBit’s rules about not targeting healthcare—as the LockBit offering deteriorates, its affiliates’ tactics may become more desperate, and harmful.
Environment scanning
![]()
The New Zealand Security Intelligence Service (NZSIS) called out China, Iran and Russia for cyber-enabled interference against both public and private sector organisations. NZSIS noted that foreign spies were targeting information about military capabilities, but also valuable IP and New Zealanders’ personal information.
![]()
A bipartisan Australian parliamentary committee recommended that social media companies be required to meet minimum transparency standards – or face fines or even bans if they do not. This follows increased government scrutiny in Australia (and elsewhere) on high-risk foreign vendor technologies and platforms, like TikTok.
![]()
With FY23 financial results now available, organisations have been given a window into the possible financial impacts of a major cyber incident. Latitude Financial disclosed a half-yearly statutory loss of $98.2 million, attributing $76 million to costs and provisions relating to the March 2023 data breach. Medibank attributed $46.4 million in cost related to its October 2022 data breach in FY 2023.
Subscribe to Cyber Adviser
Receive the latest cyber insights and expert analysis, straight to your inbox.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely Australia and New Zealand focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. We have the information, access and context to give our partners a decision advantage. Our partners receive:
- Actionable, contextualised intelligence, analysed by experts in AUNZ threat analysis.
- Sector and organisation-specific insights that are relevant and timely.
- High value, low volume artefacts that help their information overload, not add to it.
- A two-way partnership with intelligence designed for your organisation and how you plan to use it.



