Published by Governance, Risk and Compliance on 19 August 2024
ISO/IEC 27001 is an internationally recognised risk-based standard, designed to help organisations continuously manage and uplift their security posture. On 25 October 2022, the new ISO/IEC 27001:2022 standard was published, replacing the 2013 version that had remained in place for nine years. In February 2024, a further amendment was published to incorporate considerations for climate change as part of the new standard.
Organisations wanting to maintain certification to ISO 27001 must transition to the new version by 31 October 2025.

ISO 27001:2022 high level changes
- The mandatory part of ISO 27001, i.e. clauses 4 to 10 have had some minor additions.
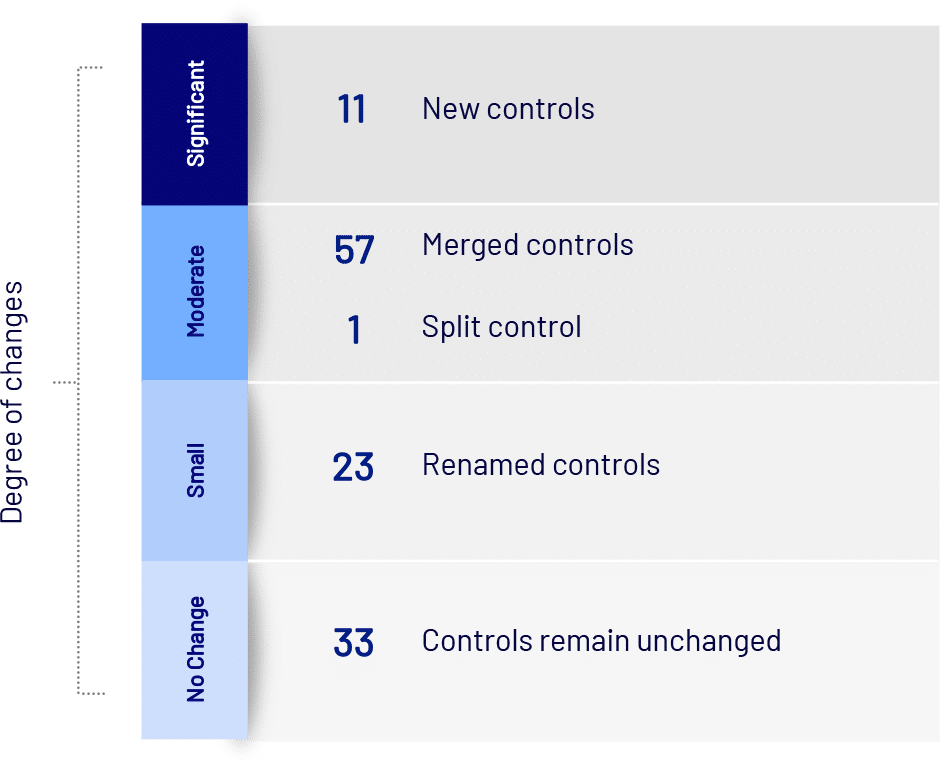
- Moderate changes have been made to security controls in Annex A.
- No controls were deleted; rather, many were streamlined from 114 to 93.
- Eleven new controls were introduced.
- Controls are now placed into four domains, instead of the previous 14.
Changes in the ISO 27001 Management System
New requirements
• Note added to 4.1 – “The organisation shall determine whether climate change is a relevant issue.”
• 4.2 c) – Requirements of interested parties that are addressed through the information security management system (ISMS).
• Note added to 4.2 – “Relevant interested parties can have requirements related to climate change.”
• Clause 6.2 – Security objectives shall be monitored.
• Clause 6.3 – Changes to the ISMS shall be planned.
• Clause 8.1 – Establishing criteria for processes and implementing control for them.
• Clause 9.3.2 c) – Changes in the needs of interested parties is a new discussion topic for management.
• Clause 10 has been restructured with Clause 10.1 and 10.2 exchanged.
Changes to the Annex A Controls
New security controls in Annex A
| Control ID | Control Title |
| A.5.7 | Threat intelligence |
| A.5.23 | Information security for use of cloud services |
| A.5.30 | ICT readiness for business continuity |
| A.7.4 | Physical security monitoring |
| A.8.9 | Configuration management |
| A.8.10 | Information deletion |
| A.8.11 | Data masking |
| A.8.12 | Data leakage prevention |
| A.8.16 | Monitoring activities |
| A.8.23 | Web filtering |
| A.8.28 | Secure coding |
Organisations certified against the 2013 version must transition to the 2022 revision by 31 October 2025.
How do I transition to ISO 27001:2022?
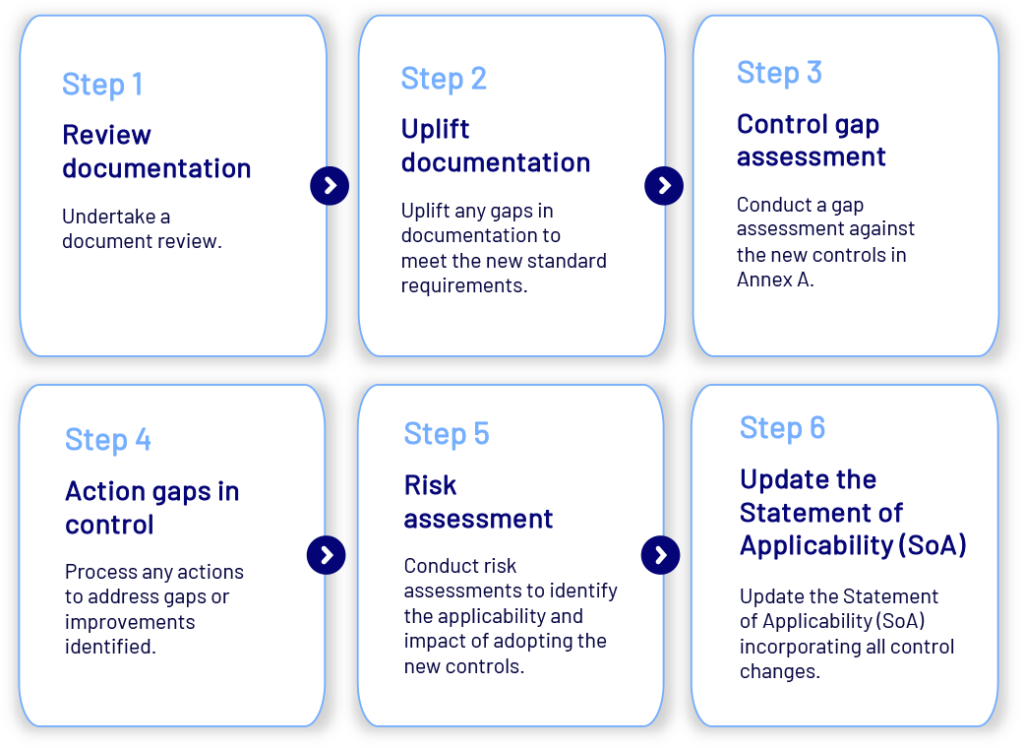
To help with the transition to the 2022 revision of ISO 27001, CyberCX recommends undertaking the following six steps before assessing your ISMS against the requirements of the 2022 standard:
1. Undertake a document review.
2. Uplift any gaps in documentation to meet the new standard requirements.
3. Conduct a gap assessment against the new controls in Annex A.
4. Process any actions to address gaps or improvements identified.
5. Conduct risk assessments to identify the applicability and impact of adopting the new controls.
6. Update the Statement of Applicability (SoA) incorporating all control changes.
Step 1 – Review documentation
All documentation used to operate the ISMS will need to be reviewed considering the changes between the 2013 version and the 2022 revision.
This includes but is not limited to:
• Information security policies;
• Procedures supporting policies;
• Documents outlining security governance;
• Operating registers; and
• Other supporting documents.
Step 2 – Uplift documentation
Documents will need to be adjusted, and then approved and communicated in accordance with document control and change management procedures. Don’t forget to remove any references to the 2013 version in the documentation.
Step 3 – Gap assessment
Conduct workshops with control owners to determine the applicability and implementation status of the 11 new controls.
Step 4 – Develop actions to address control gaps
Following step 3, formulate actions plans for any gaps identified.
Step 5 – Conduct risk assessments
Review the risk register where new controls may be applied to manage current identified risks and map controls to risks as current controls or as risk treatments where applicable.
Where new controls are mapped as risk treatments, ensure these treatments are logged in the actions register and assigned an action owner.
Step 6 – Update the Statement of Applicability (SoA)
The following steps should be considered when updating the SoA:
• For the 33 controls that have not changed, update the control IDs.
• For the 23 controls that have been renamed, update the control IDs and rename the control.
• For merged controls, change the implementation status to match the least implemented status of all the merged controls.
• For new controls, update the findings from step 3.

Don’t let your ISO Certification be withdrawn in October 2025
CyberCX provide expert assistance with ISO/IEC 27001:2022 compliance.