Published by Jed Laundry, Principal Consultant, Network and Infrastructure Solutions, 12 December 2023
A rise in attacks incorporating QR codes means it’s time to rethink how to protect ourselves from phishing emails online.
What we’re seeing
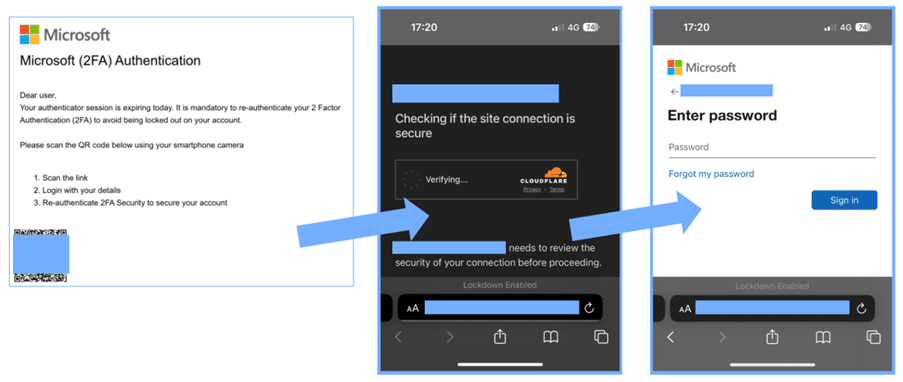
Over the past four months, CyberCX Security Operations Centres have been tracking a surge in phishing emails that ask victims to scan a QR code with their phones. These QR codes then direct users to phishing pages controlled by threat actors.
Phishing lures are typically Microsoft branded, playing on how users were previously (legitimately) instructed by IT teams to setup Microsoft Authenticator by scanning a QR code with their phone. We have also observed more generic ‘login to view this document’ lures distributed in phishing campaigns using QR codes.
Figure 1: A typical flow from initial phishing message, to anti-sandbox evasion, to MFA-aware phishing page
We have observed a particularly high rate of incidents resulting from recent campaigns using QR codes. These campaigns are particularly effective, because:
- It is more difficult for security products to detect malicious URLs in QR codes.
- Unlike traditional phishing messages where the URLs are text in the email or attachment, there is no URL for a spam filter to scan, making it more difficult to detect and disrupt.
- Initial malicious activity occurs on mobile devices, which are commonly outside of security products’ visibility and control.
- By asking the user to scan a QR code on their phone, threat actors bypass typical desktop controls: your endpoint- and network-based controls aren’t going to see the user following the links.
- Threat actors use compromised, localised mailboxes to send phishing emails.
- We have observed threat actors using compromised accounts to send these phishing emails within the same region – and by using local brands and with in-country domains, the likelihood that users will follow the lure is increased.
- Threat actors have adapted to overcoming measures that were once best-practice defences.
- Threat actors’ use of MFA-aware phishing kits, sandbox evasion techniques, and in-country IP address proxies are now mainstream, which means that if a user does follow through with entering their password and following MFA prompts, the ability to detect threat actors before they achieve their objectives is reduced.
Recommendations
So, with a rise of phishing attacks incorporating QR code technology, how can end users and individuals best protect themselves and stay ahead of the attackers? Here are some simple steps that can help.
Educate your users
If you have a user awareness training platform that sends simulated phishing emails, incorporate QR codes and use it. Platforms commonly have templates with QR codes, and QR codes can otherwise be created reasonably quickly. We recommend using updated templates in simulations and advising users of the trend towards QR code use in phishing.
User education isn’t going to be 100% effective in preventing compromise, but showing users what to look out for based on trends in threat actor behaviour can certainly increase the chances of detecting and disrupting an intrusion.
Check your Settings
Security vendors are aware of the ongoing campaigns, and some either already have or are in the process of adding QR code detection to their products. For you to get the benefit of this protection, you need to ensure your spam filter settings are in line with your vendor’s best practice recommendations.
For Microsoft E5 and Defender for Office 365, this means ensuring that your domains are configured with either the Standard or Strict preset security policies. Customers who have implemented Defender for Office 365 should review their settings, and if they haven’t already migrated to preset security policies, should do so now to take advantage of more modern capabilities.
Plan for Passwordless
While MFA is still highly recommended and is a very effective security tool for reducing credential stuffing attacks, the rise of MFA-aware phishing kits means that the overall effectiveness of push- or code-based MFA is reducing.
The next step is for organisations to move towards Passwordless solutions, where the user simply doesn’t have a password that can be phished.
Most organisations have already deployed Windows Hello across their environment, which greatly increases overall security and user satisfaction. We strongly recommend organisations start planning now on how to implement Passwordless authentication. For more information, see our previous blog Get ready to kiss passwords goodbye.
Reduce the blast radius
Finally, there will never be perfect security – we can manage residual risk by increasing the speed at which we can detect and disrupt an attack, and by decreasing the speed that a threat actor can achieve their goals.
Particularly damaging is when a threat actor compromises a user with administrative privileges. Many organisations have already taken steps to separate user and administrative accounts, and as part of developing a Passwordless strategy, organisations should consider how they further protect administrative accounts.