From Malware to Fraud – The complex world of credentials and financial theft

Published by Shameela Gonzalez, Executive Director, Industry Lead for Financial Services & Insurance and Leah Pinto, Cyber Intelligence Lead, CyberCX on 22 May 2025
In recent months, the media has surged with headlines regarding cyber threats surrounding stolen credentials. This blog post places these high-profile attacks in the spotlight, exploring their impact and steps organisations are taking against them.
Last month, a string of superannuation organisations became the latest targets of cybercriminals, sparking widespread panic among account holders who scrambled to check if their life savings were safe. It was reported the attackers used compromised credentials found on the dark web to access customer portals and attempt the withdrawal of funds.
Following the incident, the sheer volume of messages flooding my phone was overwhelming. Constant pings asking: “Did you hear about what happened to this superannuation organisation?” “Do you know what is going on?” “Should I be worried?” The endless downpour of buzzes almost left a hole in my pocket with several of these messages questioning the stability and security of the superannuation industry.
But here’s the reality — every financial institution is constantly under attack. [1]
Reports indicate that one Australian superannuation organisation was targeted by approximately 600 cyberattacks in the month of March, with the final incident being the one that drew widespread attention. As media scrutiny intensifies, the focus is widening. Researchers have uncovered credentials from at least 30,000 customers from Australia’s big four banks readily available on Telegram and the dark web. The coverage of both reports has provided a spotlight on the fragility of credentials when it comes to large scale breaches and subsequent targeted attacks.
Now here’s the thing — leaked credentials aren’t a new phenomenon.
Our CyberCX Intelligence analysts have been tracking this sort of activity for years. In the 2025 CyberCX Threat Report, our analysis identified the finance sector continuing to rank as one of the top three industries affected by cyber security incidents in Australia and New Zealand. Stolen credentials remain a leading — and growing — cause of breaches across the region.
In 2024 alone, CyberCX Intelligence analysed over 20,000 information stealer logs impacting Australian victims. Our analysis suggests approximately three quarters of credentials available online were acquired through infostealers.

What is an “infostealer”?
Infostealers are a type of malware that has been around since 2006 but during the last decade have risen in popularity among cybercriminals due to the malware’s accessibility, cost, and efficiency. Infostealers are turning personal devices into goldmines for harvesting stolen information. Think about the vast amount of personal data you store on your devices — your banking credentials, and even the logins saved within your browser for platforms like Amazon, eBay, or your favourite food delivery apps. Every time you make a transaction or store credentials, you’re creating digital footprints that, if not properly secured, leaves you vulnerable.
Cyber security threats continue to evolve, posing serious risks to financial organisations and their customers. While recent incidents in the Australian superannuation industry highlight the impact of infostealers, they’re just one part of a much larger picture. So, how deep does the issue go? Deeper than most realise — exposing not just vulnerabilities in technology but also the fine balance financial institutions tread on, in mitigating both cyber security and fraud risks. Often, being managed as distinct priorities with specialised tools and strategies.
Let’s analyse the key drivers that are exposing major challenges for FSIs:
1. Hacking, made easy
Infostealer malware has become more accessible than ever. The rise of Malware-as-a-Service (MaaS) and other “as-a-service” capabilities have made acquiring such tools alarmingly easy, with some variants available for as little as $75 AUD a month. Traditionally, hacking required deep technical expertise, but today, anyone with minimal IT skills and access to underground marketplaces can purchase sophisticated malware or other capabilities (provided their malware doesn’t also contain any nasty surprises).
This accessibility has enabled a new wave of low-level cybercriminals to launch attacks without needing to develop their own tools. With ready-made malware, user-friendly dashboards, and even customer support offered by MaaS providers, hacking has become more like a service industry. This means organisations need to be proactive, continually monitoring their external threat exposure, as part of an intelligence-led cyber security program.
2. Risky Business: Cyber Vs Fraud
Before we delve into the world of multi-factor authentication or whether industry should move towards password-less, it’s important to recognise that most large financial institutions are actively managing two distinct risks: cyber security versus fraud. As cybercrime becomes more commercialised, financial institutions face mounting pressure to defend against both cyber risk and fraud risks — two interconnected yet distinct threats. The mitigations for these risks are therefore also respectively specialised.
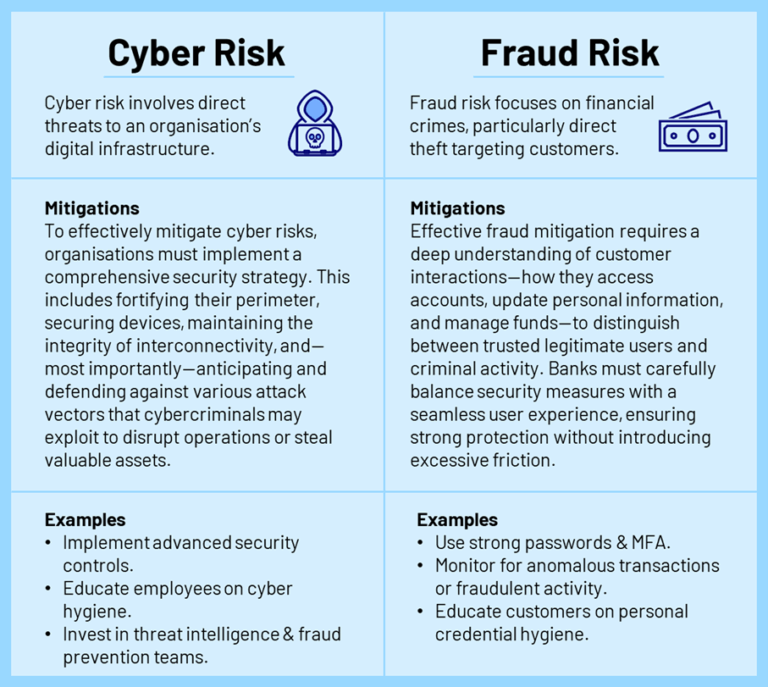
3. Drawing the Line: Cyber and Fraud Teams
Now that we have established the distinction between cyber and fraud risks, it’s important to recognise that banks, supers and insurance organisations have had to straddle the management and mitigation for each in a distinct manner noting their goal of safeguarding the financial well-being of their customers. Addressing these two distinct risks requires specialised teams dedicated to each.
To mitigate cyber risks, organisations rely on internal cyber security teams and third-party experts to identify and respond to cyber threats. These teams monitor alerts, triage incidents, and implement various cyber security controls, and must also ensure robust backup and recovery solutions should a cyber attack occur.
Cyber teams concentrate on protecting employees and organisational infrastructure.
On the other hand, fraud departments operate in a similar manner but remain distinct from cyber security teams. Their primary focus is on identifying suspicious activity related to customers, the specific analytical patterns of fraudsters and scammers and the implementation of multiple layers of controls that aim to prevent, detect or respond to a fraudulent attempt. This is achieved through transaction monitoring, identity verification, and staying up to date with real-time threat intelligence, as threat actors continually evolve their tactics — whether to steal sensitive information for future extortion or scam attempts or steal funds outright.
Fraud teams are committed to safeguarding the finances of customers.
While both cyber and fraud have distinct roles and responsibilities, both exist to provide controls and real-time detection and response to suspicious activity. To enhance effectiveness, organisations should consider factoring threat intelligence into their cyber risk management programs, ensuring proactive defence against evolving threats.
An ongoing challenge for the industry, is to identify opportunities to consolidate the management of these risks where clear overlaps and synergies exist, whilst also recognising the unique threats that need targeted mitigations.
4. Security without the Lag
A common debate in cyber security circles is whether stronger authentication controls, like multi-factor authentication (MFA), hinder workplace efficiency. While some argue that these measures create operational bottlenecks, findings from the 2025 CyberCX Threat Report reveal otherwise: MFA, when properly implemented, does not negatively impact productivity.
This insight reinforces the growing understanding that security and efficiency are not mutually exclusive.
Equivalently, when we consider how financial services institutions must navigate both customer expectations for convenience and the necessity of stringent fraud controls, it highlights the question why controls like MFA haven’t already been implemented more extensively. Certainly, post the Superannuation string of incidents, we saw multiple institutions commit to enabling MFA for every customer login (whereas the current implementations were limited to only super refunds, account changes etc.)
Banks are increasingly leveraging customer-specific digital behaviours — such as trusted devices, behavioural biometrics, and transaction patterns — to detect and respond to anomalies that could indicate fraud or scam activity whilst minimising the need for additional steps for a customer to be able to login and manage their finances.
As organisations refine their strategies, public sentiment has also shifted. While seamless, low-friction user experiences were once the priority, Australians are now more willing to accept some inconvenience to better protect their financial security. This elevated focus on security is already being implemented across organisations and is quickly becoming the standard. Customers, too, are prepared to take on some of the responsibility if it means greater protection for their funds and personal data.
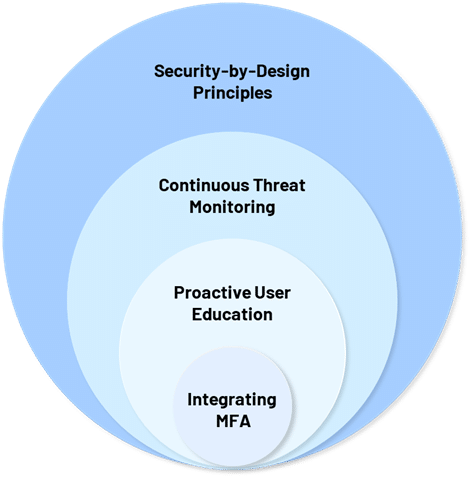
To maximise protection without impeding workflows, organisations should aim for a layered approach — integrating multi-factor authentication (MFA) with proactive user education, continuous threat monitoring, and security-by-design principles.
Each layer reinforces the next, collectively reducing risk while preserving operational agility.
The Bottom Line
CyberCX Intelligence suggest that the recent breaches we have been facing are not anomalies — there’s an evolving pattern. The good thing about patterns is that they are predictable, meaning we already know how to counter them. The rise of Malware-as-a-Service and credential theft is nothing new, and solutions exist. The challenge isn’t in finding answers — it’s in applying them consistently and proactively.
Cyber security and fraud prevention have traditionally operated in silos, with cyber teams protecting infrastructure and fraud teams monitoring financial transactions. However, access management is where their paths converge, making an effective unified approach. More so, individuals are now more aware of the risks and responsibilities involved, recognising that security is no longer just an organisational concern — it requires their active participation. As cybercriminals evolve and exploit stolen credentials with increasing sophistication, security must shift from reactive to adaptive.
The question is no longer “if” another wave of breaches will happen—it’s “when.” And when it does, those who have already strengthened their cyber and fraud resilience will be the ones standing strong.
[1] *every financial institution that requires customers to login/access personal information and finances.






