Middle East conflict: Cyber impacts of Iran-Israel military escalation

Published by Cyber Intelligence 16 April 2024
Recent direct conflict between Iran and Israel is a significant escalation in Middle East hostilities and a material change in Iran-Israel conflict. This development has cyber implications for organisations globally, including in Australia, New Zealand, the UK and US. This Intelligence Update updates CyberCX Intelligence Update: Hamas-Israel conflict, issued on 10 October 2023.
Key Points
- We assess that direct military conflict between Iran and Israel in April has materially increased cyber risk to organisations globally, for at least the next month.[1]
- Organisations with operations in Iran, Israel and surrounding countries face heightened threat of targeted disruptive and destructive cyber attacks, especially if they are in, or adjacent to, the government or critical infrastructure sectors.
- If Iran-Israel military conflict escalates further, the likelihood that organisations in third party countries will be directly targeted may also increase.
- Organisations outside of the conflict region face the following heightened cyber risks for at least the next month:
- There is a real chance (40-55%) that destructive or disruptive supply chain attacks targeting Israeli technologies could impact downstream organisations globally.
- It is unlikely but plausible (20-40%) that destructive or disruptive cyber attacks against targets in the region could spillover to organisations globally due to inadvertent miscalculation.
- There is a real chance (40-55%) that high capability and high impact tools or malware developed by well-resourced threat actors associated with the conflict could proliferate and be used against organisations globally by unrelated threat actors.
- It is likely (55-80%) that direct Iran-Israel military conflict has increased the risk that ideologically motivated threat actors will target organisations both in the region and in third party countries that condemn actions taken by Iran and/or Israel.
- Activity is likely to be limited to DDoS and defacement, but hack and leak attacks are plausible. Some ideologically motivated groups have demonstrated the ability to disrupt operational technology (OT).
- We continue to assess that pro-Russia groups, already known to target organisations globally, are likely to use the Hamas-Israel war and political responses to it as a pretext to increase their campaigns against western organisations.
Background
- The outbreak of direct military confrontation is a material change in the character of conflict between Iran and Israel. Previously, military conflict between the countries has been carried out via proxies.
- On 13 April, Iran launched a missile and drone strike against Israel, in reprisal for an Israeli airstrike against Iran’s consulate in Syria that killed seven officers of the Islamic Revolutionary Guard Corps (IRGC). The is the first time Iran has launched a military attack on Israel from Iranian soil.
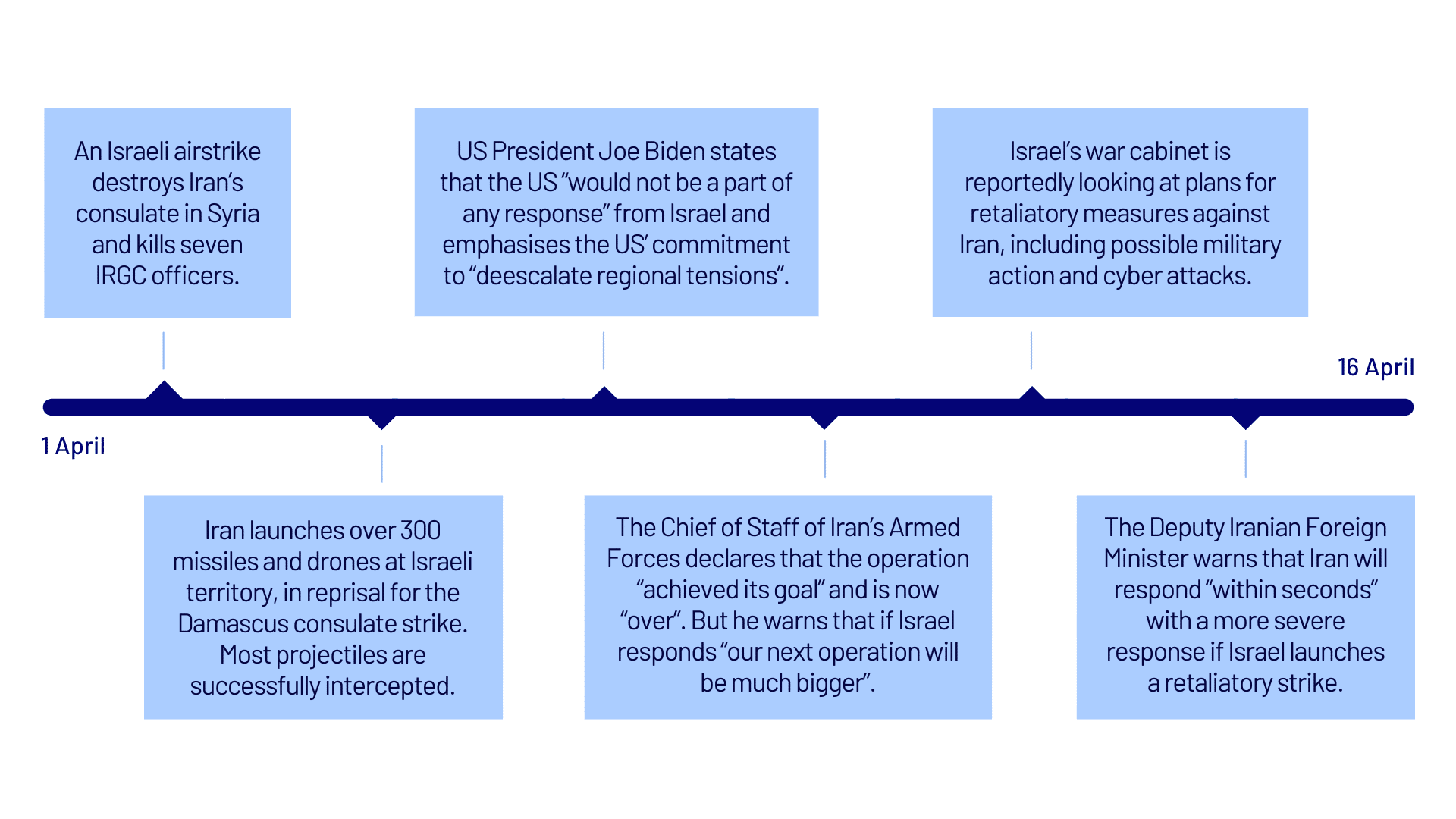
Figure 1: Timeline of Iran-Israel confrontation, April 2024
- The assessments in this Intelligence Update are consistent with CyberCX Intelligence’s ongoing assessments regarding the Hamas-Israel conflict. In October 2023, we assessed:
- The outbreak of conflict will almost certainly impact the geopolitical balance in the Middle East and have flow-on impacts globally.
- The Hamas-Israel conflict will almost certainly inflame Iran-Israel and Iran-US tensions.
- All organisations with operations in Israel or the surrounding region face heightened risk of cyber attacks, directly or indirectly.
- Any escalation or geographic widening of the conflict could result in an escalation of destructive cyber attacks, including against targets outside of the theatre of conflict.
Heightened disruptive and destructive cyber threat in Israel, Iran and surrounding region
- We assess that nation-state actors are likely (55-80%) to intensify disruptive and destructive cyber attacks in the conflict region for at least the next month.[2]
- For over a decade, Iran and Israel have engaged in tit-for-tat disruptive and destructive cyber attacks. This has intensified since the outbreak of the Hamas-Israel conflict. With the US unlikely to support any further retaliatory kinetic action by Israel, cyber attacks offer a deniable and non-kinetic targeting method to continue the tit-for-tat.
- We assess that Iran and Israel have almost certainly (95% or higher)
pre-positioned in each other’s critical infrastructure networks for use in disruptive and/or destructive operations.[3] - CyberCX Intelligence is aware of, but unable to verify, reports of Iranian-sponsored cyber attacks against Israeli critical infrastructure that coincided with Iran’s missile and drone strike. For example, Iranian group Handala claimed to have breached Israel’s radar system and disseminated 500,000 threatening texts to Israeli citizens. While we are unable to confirm the claims, we are aware of Iranian cyber threat actors exaggerating the impact of military and cyber operations via cyber-enabled influence operations for propaganda effect.
- If the current Iran-Israel direct military confrontation continues or escalates, the likelihood of cyber attacks against organisations in third party countries may increase.
- Based on available evidence, we continue to assess there is a remote chance (less than 5%) that organisations outside the immediate conflict region will be directly targeted by destructive cyber attacks associated with this conflict. This could change rapidly.
- Iran has previously launched destructive and disruptive cyber attacks against organisations in the US and Europe in reprisal for their support of Israel or other diplomatic positions.[4]
Changes to cyber threat for organisations outside the conflict region
Organisations outside of the conflict region face the following heightened cyber risks:
- It is unlikely but plausible (20-40%) that destructive or disruptive cyber attacks against targets in the region could spillover to organisations globally due to inadvertent miscalculation.
- There is a real chance (40-55%) that high capability and high impact tools or malware developed by well-resourced threat actors associated with the conflict could proliferate and be used by unrelated threat actors.
- We assess that intensified cyber conflict in the Middle East region will have flow-on impacts for organisations globally. Since October 2023, state-affiliated groups motivated by the Hamas-Israel conflict have directly and indirectly impacted organisations globally.
- We assess there is a real chance (40-55%) that destructive or disruptive supply chain attacks targeting Israeli technologies could impact downstream organisations globally.
- Since the Hamas-Israel war broke out in October 2023, we have observed Iranian nation-state actors impacting organisations in third party countries through deliberate supply chain attacks against Israeli-manufactured technology.
- For example, in November 2023 CyberCX responded to an incident involving the compromise and defacement of a Unitronics Industrial Control System (ICS) used by an Australian organisation for water management. Unitronics is an Israeli company. The defacement, which included the words “down with Israel”, was claimed by Cyber Av3ngers, an Iranian nation-state persona, and was part of a campaign that affected dozens of organisations globally. It is plausible that the level of access required to deface the impacted systems would have also enabled threat actors to send commands to attached pumps. This level of control could be used to disrupt critical systems or damage equipment.
- As significant disruptive and destructive attacks against regional targets continue, the likelihood of spillover due to inadvertent miscalculation will increase.
- For example, in February 2022 a Russian nation-state actor disrupted US-based satellite company Viasat’s KA-SAT network using the AcidRain wiper malware. While intended to aid Russia’s invasion of Ukraine, the attack impacted customers in wider Europe and likely disrupted approximately 6,000 German-owned wind turbines.
- There is a real chance (40-55%) that more advanced capabilities used by Iran or Israel could be observed and adapted by unrelated threat actors, and used against organisations globally.
- Through both the Russia-Ukraine and Hamas-Israel wars, we have observed nation-state actors, and those working on their behalf, adopting increasingly impactful destructive malware capabilities.
- In March 2024, security researchers discovered a new variant of the Russian nation-state AcidRain wiper malware, called AcidPour. AcidPour was discovered by a user geolocated in Ukraine uploading a sample to a public malware sandbox, making it potentially accessible to a wide range of threat actors.[1]
Ideologically motivated threats persist
- We assess that direct Iran-Israel military conflict has increased the likelihood that ideologically motivated threat actors will target organisations in the conflict region and in third party countries which provide military or diplomatic support.
- Ideologically motivated actors continue to favour DDoS and defacement, but claimed hack-and-leak attacks are increasingly common for pro-Palestine groups. Some ideologically motivated groups have also demonstrated the ability to disrupt OT.
- For example, in December 2023, pro-Iran group Haghjoyan claimed access to ICS related to building management systems in the We are unable to verify Haghjoyan’s claims, but ideologically motivated groups are known to inflate or fabricate claims to generate publicity, which in and of itself can generate public concern and unrest.
- Since October 2023, we have observed pro-Russia and pro-Hamas groups targeting organisations globally, including in Australia, New Zealand, the UK and the US. The
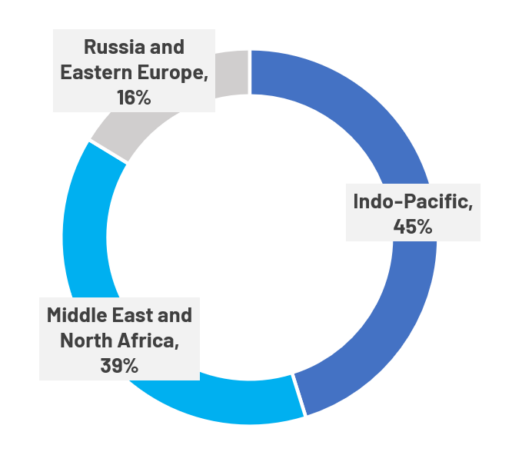
Hamas-Israel war has significantly expanded the hacktivist ecosystem.- Since the Hamas-Israel conflict broke out in October 2023, we have tracked at least 207 anti-Israel channels on Telegram, dispersed globally (see Figure 2).
- 51 per cent of the Telegram channels tracked by CyberCX Intelligence appear motivated by the Hamas-Israel war, compared to 19 per cent for the Russia-Ukraine war. However, we note that some pro-Russia groups have engaged on issues related to both wars.
- This includes groups like Anonymous Sudan, which conducts attacks in support of both Russia and Hamas, has Russian state affiliations, and is known to have access to more resourced and impactful DDoS capability and tooling.[6]
- We continue to assess that pro-Russia groups already known to target organisations globally are likely to use the Hamas-Israel conflict, escalating Iran-Israel tensions, and diplomatic responses to both as a pretext to increase their campaigns against western organisations.
- Ideologically motivated actors continue to favour DDoS and defacement, but claimed hack-and-leak attacks are increasingly common for pro-Palestine groups. Some ideologically motivated groups have also demonstrated the ability to disrupt OT.
Figure 2. Geographic breakdown of anti-Israel channels tracked by CyberCX Intelligence
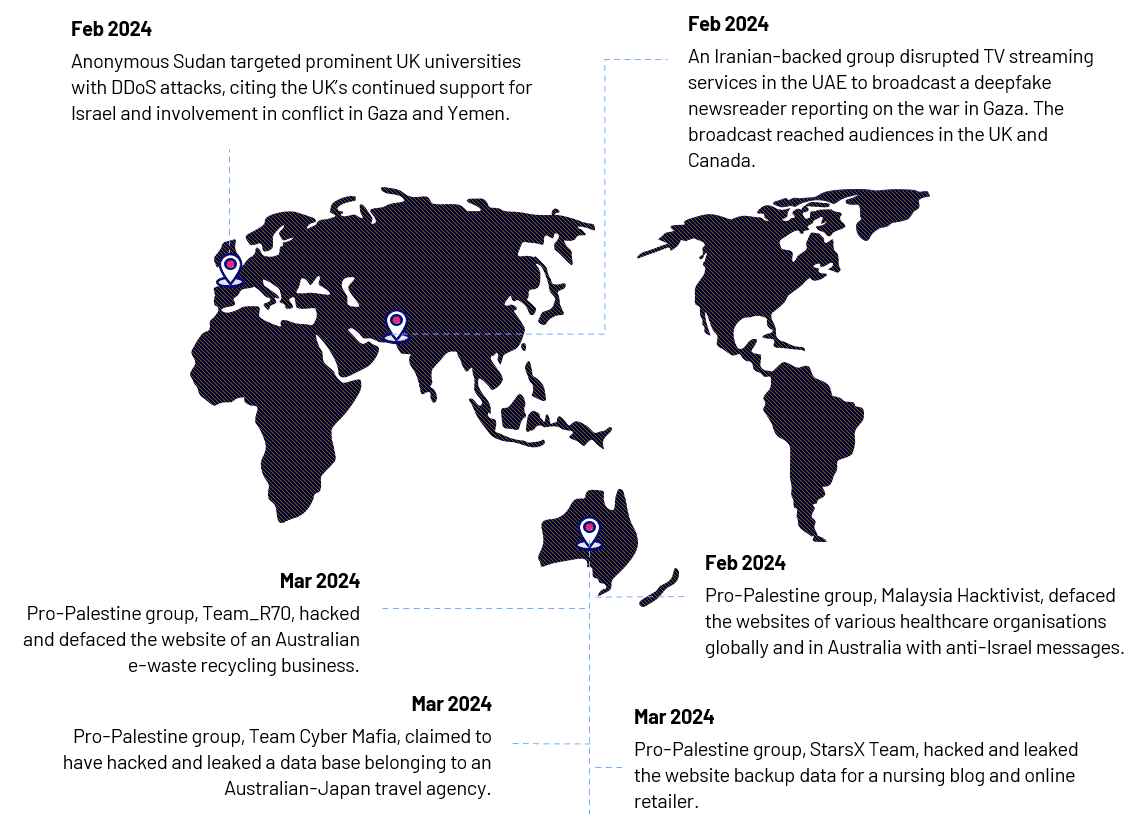
- Ideologically motivated actors are largely opportunistic, and target organisations because of their geography and vulnerability. Figure 3 shows the breadth of targeting of organisations in third party countries motivated by the Hamas-Israel conflict in 2024.
- Opportunistic attacks are unpredictable. CyberCX Intelligence continues to urge all organisations to review controls related to DDoS mitigation and website defacement.
Figure 3. Sample targeting of western organisations by groups motivated by the Hamas-Israel conflict in 2024
[1] This assessment is made with moderate confidence.
[2] This assessment is made with moderate confidence.
[3] In February 2024, Google reported that Iranian nation-state actors conducted cyber-enabled espionage and pre-positioning in Israeli networks for years in the lead up to the breakout of the October 2023 Hamas-Israel war. See: https://blog.google/technology/safety-security/tool-of-first-resort-israel-hamas-war-in-cyber/
[4] As recently as February 2024, the Albanian government, supported by NATO, the UK and US, attributed cyber attacks on government organisations to Iran, following longstanding diplomatic conflict.
[5] https://www.sentinelone.com/labs/acidpour-new-embedded-wiper-variant-of-acidrain-appears-in-ukraine/
Guide to CyberCX Intelligence reporting language
CyberCX Cyber Intelligence uses probability estimates and confidence indicators to enable readers to take appropriate action based on our intelligence and assessments.
| Probability estimates – reflect our estimate of the likelihood an event or development occurs | ||||||
| Remote chance | Highly unlikely | Unlikely | Real chance | Likely | Highly likely | Almost certain |
| Less than 5% | 5-20% | 20-40% | 40-55% | 55-80% | 80-95% | 95% or higher |
Note, if we are unable to fully assess the likelihood of an event (for example, where information does not exist or is low-quality) we may use language like “may be” or “suggest”.
| Confidence levels – reflect the validity and accuracy of our assessments | ||
| Low confidence | Moderate confidence | High confidence |
| Assessment based on information that is not from a trusted source and/or that our analysts are unable to corroborate. | Assessment based on credible information that is not sufficiently corroborated, or that could be interpreted in various ways. | Assessment based on high-quality information that our analysts can corroborate from multiple, different sources. |