Intelligence Update. A question of timing: examining the circumstances surrounding the Nauru Police Force hack and leak

CyberCX Cyber Intelligence is actively monitoring the cyber threat landscape for threats associated with Australia’s upcoming federal election. This Intelligence Update provides situational awareness of the cyber activities surrounding a recent leak of sensitive emails allegedly held by the Nauru Police Force. CyberCX has not reviewed the contents of the stolen emails in detail and does not intend to. This Update focuses on anomalies in the leaker’s activities that warrant scepticism about their motivations, the integrity of the leaked data and further investigation by journalists and other experts.
Key Points
- On 2 May 2022, 285,631 files stolen from the Nauru Police Force, including some relating to alleged human rights abuses in Australia’s offshore processing centres, were leaked.
- CyberCX assesses that the leak, published less than three weeks before an Australian federal election—and exactly one week before early voting opened—is intended to influence Australian politics. The leak also comes at a time of diplomatic tension between Australia and other Pacific countries, particularly Solomon Islands.
- At this time, there is insufficient evidence to definitively attribute this incident. CyberCX has high confidence that it was not conducted by hacking collective Anonymous as some media outlets have claimed.
- There are several anomalies that invite scepticism about the motivations of the threat actor and the integrity of the leaked data that warrant further investigation.
- Hack-and-leak operations are criminal activities (unlike whistleblowing, journalism or political speech) and have been used by malign actors to undermine open and transparent political debate and democratic processes, including elections.
Background
- At 9:19 PM AEST on 2 May, 79.4GB of confidential emails alleged to belong to the Nauru Police Force were leaked on Enlace Hacktivista. Enlace Hacktivista is a relatively new wiki-based website positioned as a leak site for hacktivists and whistleblowers.
- Two hours following the leak on Enlace Hacktivista, the leak was republished on the Distributed Denial of Secrets (DDoSecrets) site. DDoSecrets is a high-profile wiki-based leak site run by US-based journalists.
- The leak contains 285,631 files from 126 email mailboxes. This is sizeable given that the Republic of Nauru, a tiny island nation, has a population of only 10,000.
- The threat actor behind the leak appears to be politically-motivated. The leak was accompanied by a statement calling for the “newly elected Australian government” to end mandatory detention of asylum seekers and investigate abuse by the end of 2022.1 The statement is phrased as a request and does not threaten consequences for inaction. The threat actor alleges that the leaked emails document abuse against asylum seekers and refugees in Nauru. CyberCX has not reviewed the contents of the emails in detail.
- The threat actor did not indicate any alignment with any particular group or cause. Open source reporting has attributed the threat actor to the Anonymous collective.2 CyberCX has not identified any information to connect the leak to Anonymous. CyberCX assess attribution to Anonymous is a result of misreporting or ‘click-baiting’ that incorrectly claimed the threat actor’s statement was signed off as “Anonymous!”.3 This sign off does not appear in the threat actor’s original statement.
Unusual Timeline
CyberCX has developed the following timeline of the Nauru Police Force data leak.
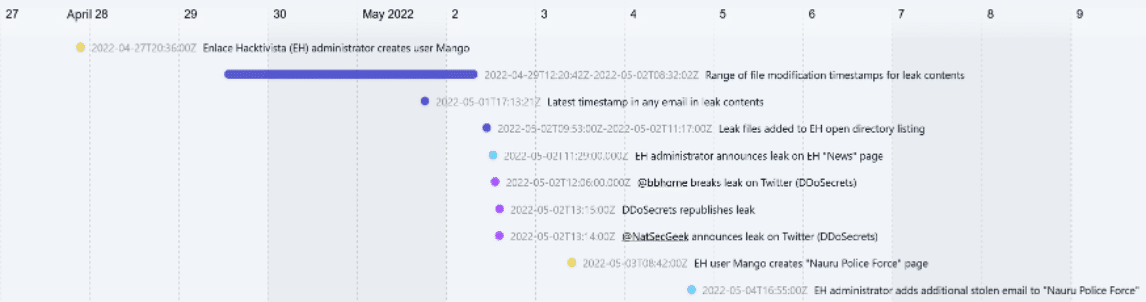
- The threat actor highly likely concluded staging data for exfiltration at or shortly after 17:13:31 UTC on 1 May 2022 (03:13:31 AEST on 2 May 2022). This is the last timestamp that appears in any email within the leaked data. If the information published represents the total stolen data, the threat actor must have been staging data at or after this timestamp. The threat actor likely finished staging data shortly following this timestamp, before a subsequent email was sent or received by Nauru Police Force and exfiltrated and included within the leaked data.4
- It is highly likely that Enlace Hacktivista published the stolen emails at most 16 hours and 39 minutes after the threat actor finished exfiltrating data. Enlace Hacktivista added files to an open directory on a subdomain of its website5 starting from 09:53 UTC on 2 May 2022 (19:53 AEST on 2 May 2022) and ending at 11:17 UTC on 2 May 2022 (21:17 AEST on 2 May 2022).
- There is evidence that Enlace Hacktivista published the leak only 81 minutes after the threat actor concluded handling stolen files. Files contained within the .zip archives leaked by Enlace Hacktivista have file modification timestamps ranging from 12:20:42 UTC on 29 April 2022 (00:20:42 AEST on 30 April 2022) at the earliest to 08:32:02 on 2 May 2022 (18:32:02 AEST on 2 May 2022) at the latest. There is an 81 minute period between the latest timestamp in the .zip archives and the earliest files being published to Enlace Hacktivista’s open directory. This assessment is made with low confidence because the system time on the device used to archive the leak is unknown and modification times may not reflect the actual last modification of the content.
- There is a real chance that the threat actor maintained access to Nauru Police Force and exfiltrated additional data after the leak was published. At 16:55 UTC on 6 May 2022 (06:55 AEST on 6 May 2022) the Enlace Hacktivista administrator posted the body-text of an additional email to the “Nauru Police Force” page. The email is purportedly an email between the Nauru Police Force Commissioner and the Nauru Secretary. The email refers to Nauru Police Force’s progress with responding to the data breach.
- There is also a real chance that the threat actor responsible for the leaks, or another threat actor, gained access to Nauru Police Force networks before the events in the timeline (see Threat actor statement).
- It is likely that an Enlace Hacktivista member conducted the hack and/or that the Enlace Hacktivista administrator was aware of the hack while it was occurring. The short lapse in time between exfiltration and publication is inconsistent with the threat actor establishing contact with Enlace Hacktivista and transferring data after concluding data exfiltration. This short lapse in time is also atypical of ideologically-motivated data leaks, especially because of Enlace Hacktivista’s obscure status prior to this leak.
- CyberCX assess with low confidence that the Enlace Hacktivista account “Mango” belongs to the threat actor. This finding is determined on the basis that the Mango account was created at 20:36 UTC on 27 April 2022 (06:36 AEST on 28 April 2022) and its contributions to Enlace Hacktivista have focused on the Nauru Police Force leak.
Threat Actor Identity and Motivations
Enlace Hacktivista
- Enlace Hacktivista (Spanish for ‘Hacktivist Link’) is an English-language wiki-based leak site and self-proclaimed hacker news forum.6
- Enlace Hacktivista does not have a set of editorial standards or data source disclaimers and does not advise its users not to commit crimes to publish data. The site also includes instructional hacking material.
- Enlace Hacktivista’s domain was first observed on 21 December 2021. The first contributions were made to Enlace Hacktivista’s wiki on the same date. Enlace Hacktivista is hosted by Icelandic pro-free speech provider, FlokiNET. FlokiNET has claimed it has recently refused a request from the Australian Federal Police to take the Nauru Police Force leak down from Enlace Hacktivista.7 This claim has not been verified.
- Enlace Hacktivista had a low public profile prior to the Nauru Police Force hack and leak—it was relatively new and had not been connected to a significant incident. Prior to the Nauru Police Force hack and leak, Enlace Hacktivista had been mentioned only six times on Twitter8 and had not been Google searched enough to register on Google trends.
- On 6 March 2022, Enlace Hacktivista was first to report the hack of Guatemalan mining company Pronico as an environmental protest. The Spanish-language hacktivist group Guacamaya took credit for the hack. A period of 19 days elapsed between the Pronico hack and its reporting on Enlace Hacktivista.
- The Pronicio and Nauru Police Force hacks are the only incidents where first reports can be attributed to Enlace Hacktivista.
- It is likely that unmoderated account creation on Enlace Hacktivista was open to the public for a maximum of eight weeks until 22 February 2022. Since then, new users must contact the administrator to request an account.
- Enlace Hacktivista is operated by a person or persons unknown and does not appear to be a large or popular community.
- Enlace Hacktivista has a low rate of sequential edits to pages and low levels of concurrent user activity.
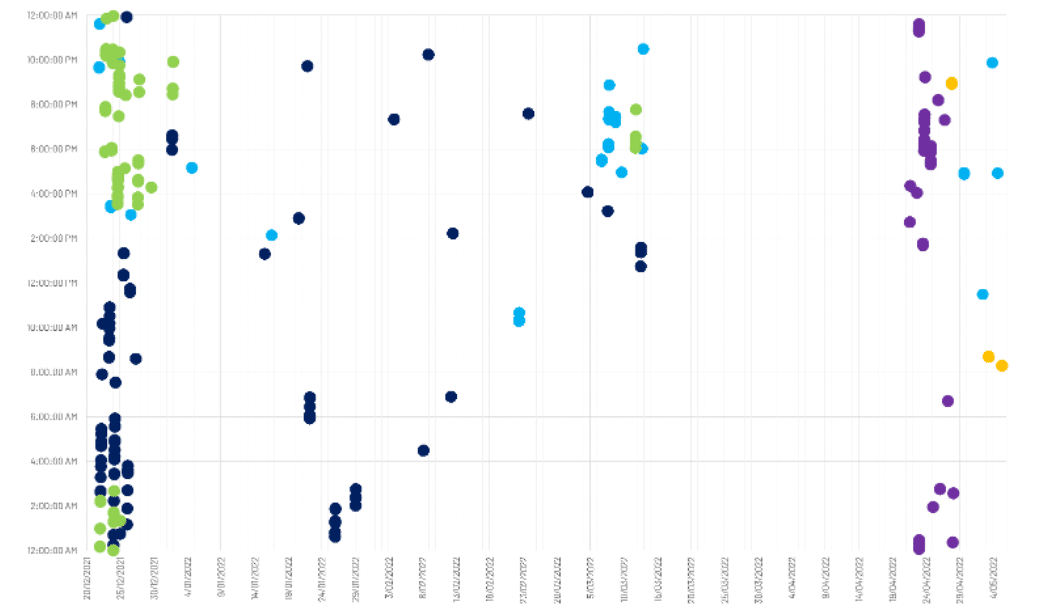
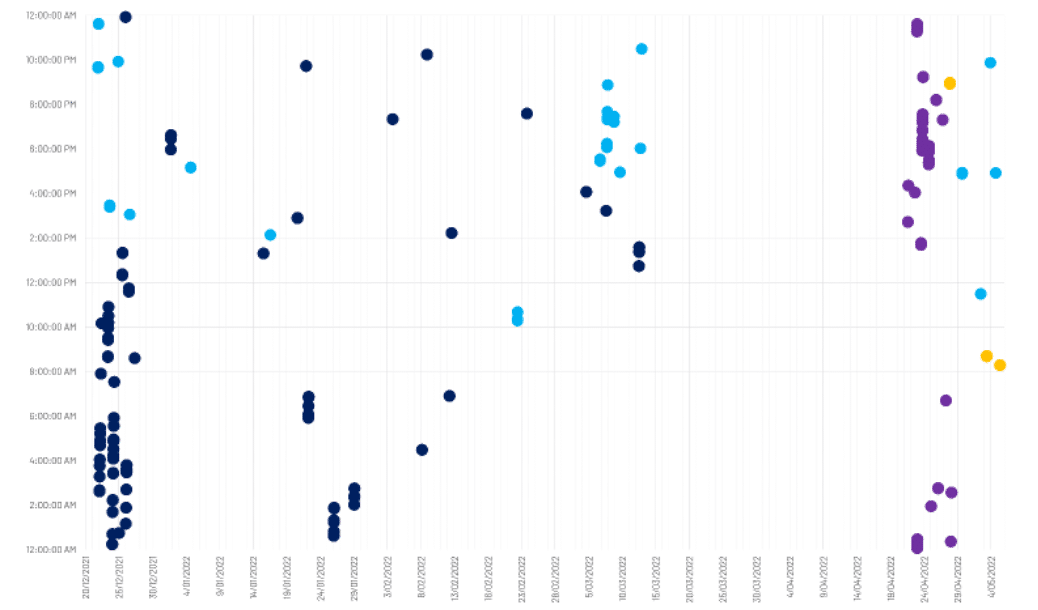
- Based on contribution pattern, it is likely that the administrator of Enlace Hacktivista operates at least two separate accounts on the site to make contributions.
- The user ‘Mx Yzptlk’ accounts for 100% of instances in which two Enlace Hacktivista accounts have ever been concurrently active.
- The five accounts active on Enlace Hacktivista have made a total of 353 contributions to 79 pages during Enlace Hacktivista’s 20 week operating history.9
- CyberCX has insufficient evidence to assess whether Enlace Hacktivista is a ‘sockpuppet10’ rather than a genuine site for leaks or whistleblowers. This is a key intelligence gap that warrants further investigation.
DDoSecrets links with Enlace Hacktivista
- DDoSecrets is a high-profile leak site based in the US. DDoSecrets is a registered non-profit organisation with transparent funding and membership.11 DDoSecrets has a charter of journalistic standards and provides disclaimers in relation to data that may be supporting an information warfare objective.12 DDoSecrets also advises prospective sources not to commit crimes in order to provide information.13
- Enlace Hacktivista implements none of DDoSecrets transparency measures and does not exercise a separation between publisher and ‘source’. Enlace Hacktivista is likely directly connected to threat actors, including while threat actors are committing crimes. As such, information it publishes should be regarded with scepticism, in terms of both data integrity and representations by threat actors (including their stated identity and motivation).
- CyberCX assess with high confidence that DDoSecrets co-founder and journalist, Emma Best, is active on Enlace Hacktivista. Best has publicly referred to posting under the handle ‘Mx Yzptlk’14 and the same handle is used by Best on DDoSecrets. CyberCX has no evidence to indicate that Best was involved in the hack of the Nauru Police Force and does not suggest she has engaged in any wrongdoing.
- Mx Yzptlk has made 39% of all contributions to Enlace Hacktivista and first contributed on 22 December 2021, approximately three hours after the first ever contribution to the site.
Threat Actor Statement
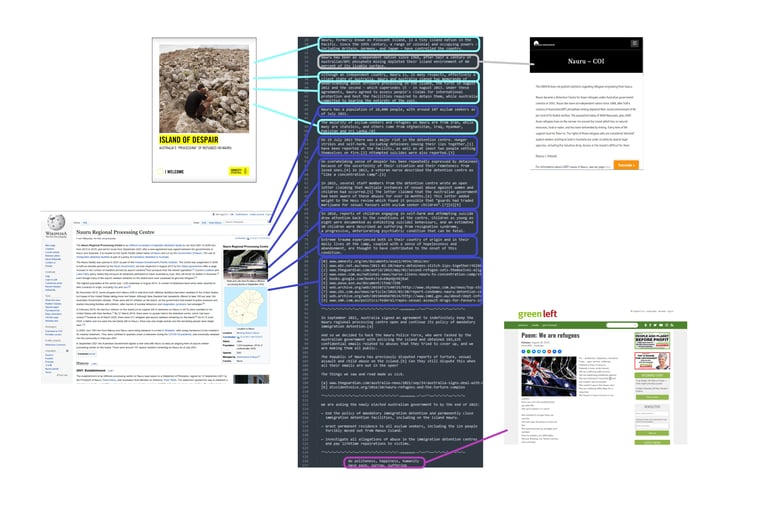
- The threat actor released a 954 word statement alongside the leak. The statement includes an account of alleged human rights abuses and controversies related to the Nauru Regional Processing Centre. The threat actor does not directly refer to any information contained within the stolen emails.
- Approximately 60% of the statement comprises sentences copied verbatim from other sources. Copied material is mixed between and within sources at the paragraph and sentence level.
- The most recent event referred to by the threat actor is the Australian Government’s closure of the Manus Island Regional Processing Centre in October 2021. All sources referred to in the statement have been publicly available since September 2021.
- The statement invites scepticism about the threat actor’s motivation and warrants further investigation.
- Plagiarism could indicate that the threat actor is not motivated by personal activism, is not a native English speaker, or is simply an attempt to obfuscate their style. CyberCX has insufficient evidence to assess the credibility of these hypotheses.
- The publication dates of the source material could indicate that the threat actor was planning the leak operation since at least September 2021, and possibly had access to Nauru Police Force at this time, but waited to exfiltrate and publish the data at a time when it would have maximum influence on Australian politics.
Political and Geopolitical Context of the Hack and Leak
The leak invokes sensitive, long-standing political issues in Australia under three weeks before an Australian federal election and one week before early voting opened.15
- Politically- or strategically-motivated threat actors capitalise on elections to maximise impact. Threat actors exploit information and sensitive issues in election contexts to maximise their impact on core issues, ‘weaponising’ controversial political decisions and debates to attract media attention, influence public discourse and, sometimes, to degrade trust in democracy.
- Alleged human rights abuses in offshore processing centres in Nauru have long been a controversial topic in Australian public and political debate. This is not the first time Nauru has been targeted in hack-and-leak operations.
- In 2013, Anonymous conducted a cyber attack against Nauru government infrastructure that shut down email and government services for at least four hours.16 The hack was allegedly in response to the Nauru Government’s handling of a riot that took place in the Nauru Regional Processing Centre.
- In August 2016, more than 2,000 incident reports from the Nauru Regional Processing Centre were leaked.17 This leak coincided with the finalisation of election writs for the Australian federal election held in July 2016.18
- The nature of the demands made by the threat actor behind the Nauru Police Force leak indicates an intent to influence Australian political discourse rather than achieve the claimed human rights objective.
- The threat actor calls for the permanent closure of immigration detention facilities, including on Nauru. However, in March 2022, Australian Prime Minister Scott Morrison agreed to a resettlement deal with New Zealand that will remove all refugees from Nauru over the next three years to resettle in New Zealand.19
- The threat actor does not threaten any consequence if its demands are not met or specifically refer to any allegations contained in the stolen data itself.
The leak occurred against the backdrop of increasing geopolitical tension in the Indo-Pacific and focus on Australia’s diplomatic relationships with countries in the Pacific.
- Australia and Nauru share a longstanding relationship built on cooperation. Most recently on 28 February, the Australian Foreign Minister, Marise Payne, announced that Australia would provide a $40 million grant finance package to Nauru, including $30 million through the Australian Infrastructure Financing Facility for the Pacific.20 The Australian Federal Police works very closely with the Nauru Police Force.21
- The Pacific is increasingly a site of geopolitical contest and friction between many nation-states.
- For example, the recent signing of the China-Solomon Islands Security Agreement indicates an accelerated shift by China towards strategic interest in the Pacific region. That agreement has triggered significant media and political attention in the lead up to the federal election. Relations between Solomon Islands and Australia have rapidly deteriorated since a draft of the agreement was leaked in March 2022, with the Solomon Islands Prime Minister recently claiming his country has been threatened with invasion by Australia.22
Hacktivism is increasingly prominent in the global cyber threat landscape.
- In connection with the Russia-Ukraine war, there has been an uptick in public interest and publicity-focused activities from independent hacktivist groups that are not directly connected to nation-states.
- Hacktivism and hack-and-leak operations are criminal activities that can have significant consequences, particularly in times of escalated geopolitical tension and conflict. These approaches are distinct from genuine and lawful journalism or disclosures by whistleblowers.
- Nation-state actors have an established history of using hacktivist cover to influence public discourse about controversial and political events, including in election contexts.23 This heightens the need to subject claimed hacktivist activity to objective scrutiny and highlights the importance of understanding the motivations and identities of hack-and-leak threat actors. CyberCX has not identified any information to directly link the Nauru Police Force hack-and-leak to a nation-state actor.
This Intelligence Update has been prepared by the CyberCX Cyber Intelligence Team.
Read more about our practices and insights:
If you need assistance responding to a cyber incident, please contact our investigation and response team here.
Guide to CyberCX Cyber Intelligence reporting language
CyberCX Cyber Intelligence uses probability estimates and confidence indicators to enable readers to take appropriate action based on our intelligence and assessments.
| Probability estimates – reflect our estimate of the likelihood an event or development occurs | ||||||
| Remote chance | Highly unlikely | Unlikely | Real chance | Likely | Highly likely | Almost certain |
| Less than 5% | 5-20% | 20-40% | 40-55% | 55-80% | 80-95% | 95% or higher |
Note, if we are unable to fully assess the likelihood of an event (for example, where information does not exist or is low-quality) we may use language like “may be” or “suggest”.
| Confidence levels – reflect the validity and accuracy of our assessments | ||
| Low confidence | Moderate confidence | High confidence |
| Assessment based on information that is not from a trusted source and/or that our analysts are unable to corroborate. | Assessment based on credible information that is not sufficiently corroborated, or that could be interpreted in various ways. | Assessment based on high-quality information that our analysts can corroborate from multiple, different sources. |
1] https://ddosecrets.substack.com/p/nauru-police?s=r
2] See, e.g., https://twitter.com/YourAnonTV/status/1521870859107020802
3] https://www.hackread.com/anonymous-leak-police-emails-australia-offshore-detention/
4] Nauru Police Force operates night shifts and is likely to have email activity throughout a 24 hour period. See, e.g., http://ronlaw.gov.nr/nauru_lpms/files/gazettes/df95014e184d17e77f5374f0c41f0d87.pdf
5] We assess that Enlace Hacktivista’s website timestamps are highly likely in the UTC time zone. This assessment is based on cross referenced activity on the website with other sources, including social media posts by a likely member of Enlace Hacktivista and cached versions of the website captured by various open source scrapers showing snapshots of activity.
6] https://www.enalcehacktivista.org
7] https://twitter.com/FlokiNETehf/status/1521836418951270400
8] https://twitter.com/search?q=%22enlacehacktivista%22%20until%3A2022-05-01%20since%3A2007-01-01&src=typed_query&f=top
9] This analysis does not include several advertising spam accounts that appear to have been registered to the site and subsequently detected in February 2022.
10] An online identity created, and used, for purposes of deception
11] https://ddosecrets.com/wiki/About
12] https://ddosecrets.com/wiki/Category:Cyberwar
13] https://ddosecrets.com/wiki/Frequently_Asked_Questions
14] https://twitter.com/NatSecGeek/status/1502352462220570631
15] Up to 50% of Australians are expected to cast their votes in the federal election before election day: https://www.aph.gov.au/About_Parliament/Parliamentary_Departments/Parliamentary_Library/FlagPost/2022/May/Early_voting_at_the_2022_federal_election
16] https://www.dailydot.com/unclick/anonymous-hack-nauru-australian-immigration/
17] https://www.theguardian.com/australia-news/2016/aug/10/the-nauru-files-2000-leaked-reports-reveal-scale-of-abuse-of-children-in-australian-offshore-detention
18]https://www.aph.gov.au/About_Parliament/Parliamentary_Departments/Parliamentary_Library/pubs/BriefingBook45p/FederalElection2016#:~:text=The%202016%20federal%20election%20was%20the%20first%20double,as%20the%20most%20prominent%20issue%20in%20the%20campaign.
19] https://www.afr.com/politics/federal/policy-backflip-to-remove-all-refugees-from-nauru-20220324-p5a7fb
20] https://www.foreignminister.gov.au/minister/marise-payne/media-release/joint-statement-australia-nauru-cooperation-critical-transport-infrastructure
21] http://naurugov.nr/government/departments/nauru-police-force/australian-federal-police-(afp).aspx
22] https://www.abc.net.au/news/2022-05-04/solomon-islands-manasseh-sogavare-criticises-west-praises-china/101038296
23] https://www.sentinelone.com/labs/hacktivism-and-state-sponsored-knock-offs-attributing-deceptive-hack-and-leak-operations/







